- What is Hush?
- Criticism of Zcash and the trusted ceremony
- New and Noteworthy Developments for HUSH
- Where can I buy HUSH
- Where can I store HUSH
- How to mine HUSH
- Conclusion
What is Hush?
Launched on November 21, 2016, Hush is a token, secure messaging platform, and fork of the Zcash 1.0.9 codebase. As its own unique blockchain network, HUSH acts as not only a store of value but a medium of exchange for using the secure messaging platform. This “messaging” function is also the mechanism for sending and receiving transactions.
Key Hush Stats
Symbol: HUSH
Algorithm: Equihash
Block Time: 2.5 minutes
Block Reward: 12.5 Hush rewarded per block discovered by miners
Difficulty Adjustment: Every block, Digishield V3
Reward Halving: Every 4 years (same as Bitcoin)
Total Coin Supply: 21,000,000 (same as Bitcoin)
Pre-mine: 0.578% (121475 HUSH)
https://files.coinmarketcap.com/static/widget/currency.js
Before we get into the weeds of Hush, it’s important for you to understand this very important but often overlooked concept: metadata.
Metadata is a valuable digital footprint and data stash we generate from our daily digital activity.
Companies are building billion dollar empires on, wait for it…our personal data. We don’t even need to do anything to create this data or value (other than live life as usual). Despite seeming unimportant, this information is highly sought after by corporations and other eager entities who are willing to pay top dollar for it.
But, why do they want this information? Because it’s a veritable treasure trove of our thoughts, feelings and most importantly, behaviors. Think about how useful knowing your spending habits would be for a seller to your market demographic. From that information, companies can target us with products, services and other forms of advertising and agenda driven communications to their heart’s’ content.
Hush aims to provide protection by anonymizing this metadata at a protocol level ultimately protecting even the most novice user with this built-in privacy backbone.
Built within Hush is HushList, a customized secure protocol and private messenger which allows you a contact list of infinite receivers. HushList receivers must always be zaddrs (therefore anonymous). The user can opt to send from a taddr pseudonymous address.
Your Hush contacts are stored locally on your computer, and messages, aka HushList memos, are stored in the blockchain, encrypted so that only the receiver’s private key can decrypt it.
With HushList, financial transactions are messages under a pseudonym “user” name or undisclosed anonymous participant. Text and binary documents can be appended to these messages which facilitates a censorship-resistant storage unit of information.
Using the ZCash protocol, transactions can be shielded or made transparent. The key differentiators are how Hush hides all the metadata and interoperates with forks.
Unique features of Hush
- Compatibility with Zcash forks, including Zcash, Zclassic, ZenCoin, Komodo (any of their asset chains), Zerocoin and future forks. There may be minor tweaks required depending on the fork but ultimately HUSH aims to seamlessly allow this interoperability.
- New security and full stack technology including TLS (transport layer security) as well as TOR nodes and bitcore. Originally ported over from ZenCash with modifications, this security layer helps protect users identities (such as IP addresses) and other data at a protocol level. This means privacy is built-in to the system from the ground up.
- A counterparty port which allows private and public asset issuance. Use cases include support for Ethereum developers, who can easily author smart contracts on Hush.
Hush is considered more of a fair launch due to the community openness as opposed to the Zcash private, closed funding approach. The developers did very low pre-mine (.578% of the total supply) which they disclosed prior to launch. In addition, Hush maintains its position as a top Equihash algorithm coin for miners. Ultimately, the project has created a bit of an underdog persona with a LOT of grassroots acclaim from community members.
“I am a big fan of the philosophy that we need as many good cryptocoins as possible to replace the global credit card transaction volumes. You could say I am an altcoin maximalist. So my hope is that Hush and Bitcoin Hush are some of those “good coins” because they have some of the best tech of any of their competitors and we have a friendly and welcoming community. Also, Hush is not controlled by any for-profit or non-profit company/organization.” ~Jonathan “Duke” Leto, Hush Core Developer
Criticism of Zcash and the trusted ceremony
With Zcash there was a ceremony of destroying the private keys (aka toxic waste) which would allow a would-be attacker to create duplicate coins on the network. The specific details: multiple people (pre-chosen participants of the ceremony) each generated a “shard” or partial section of a public/private key pair (which if brought together would grant the users “backdoor” access to the network).
The participants then destroyed their private key shards and kept the public key one. The public key shards were brought together to form the public view key parameters.
Hush used the same “sprout proving key” procedure and process as Zcash did, however, Hush went the additional mile with security through protocol level architecture (TLS, TOR etc). At worst an attacker could simply counterfeit Zcash (or the respective forked coin like Hush) but the users’ privacy would remain intact regardless.
Duke Leto comments further: “All that really means is that there would be MORE Hush in existence, potentially, and people could do more HushList protocol memos with this toxic waste. No HushList memo’s encryption would be broken, no memos would be made public that were private. So yes, Toxic Waste is very concerning from the “invisible dilution” viewpoint, but from the viewpoint of a utility coin that enables private communication, Toxic Waste is not very concerning. And just to clarify even more, if “toxic waste” existed for Zcash, that evil party could use that to create money on basically every modern Zcash fork (everything using the Sprout Key), not just Zcash itself.”
[thrive_leads id=’5219′]
New and Noteworthy Developments for HUSH
- New Hush Web Wallet – Now you can access your Hush in the Cloud through any browser. Hush also merged the latest Bitcore and transport layer security (TLS), which supports shielded transactions in the web wallet in the near future.
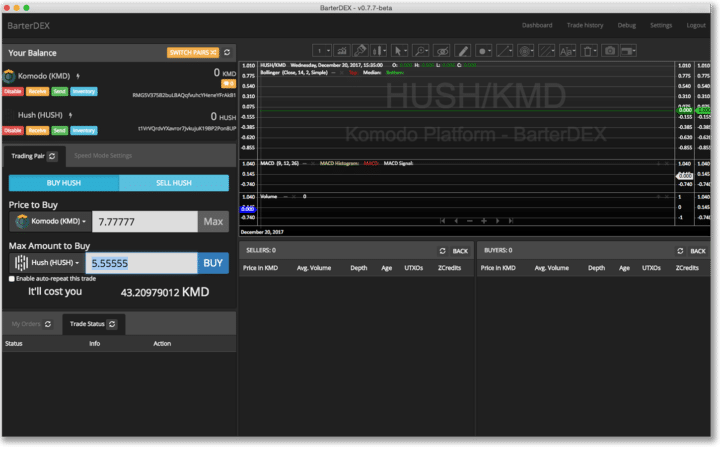
- Komodo (KMD) – A decentralized exchange (DEX) built on the code fork of Zcash which includes delayed-Proof-of-Work and Asset Chains. It also allows issuing of new tokens. Komodo is considered a sister coin to Hush with significant crossover in the mining and developer communities. Rather than reinvent the wheel to create a new mainnet+testnet, Hush used KMD Asset Chains, automating the process into one easy to run command line.
The HUSH BarterDEX based on Komodo (KMD)
Where can I buy HUSH
There are two main exchanges that carry Hush: Cryptopia which is a centralized exchange out of New Zealand and the BarterDEX which is a decentralized exchange based on Komodo (KMD).
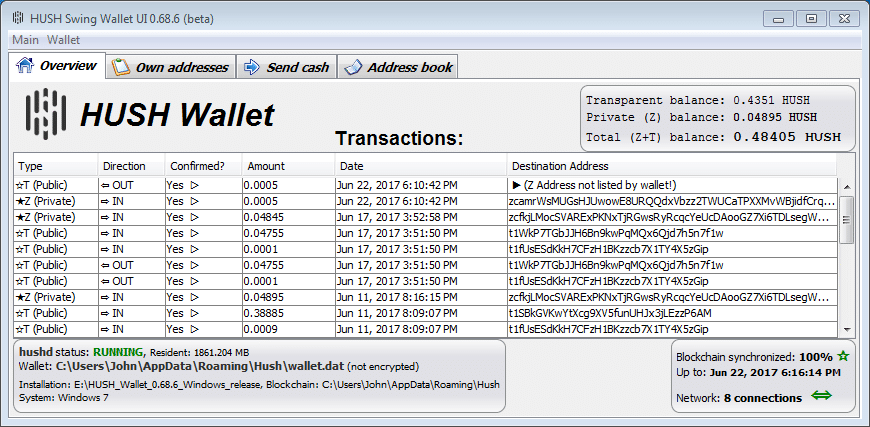
Where can I store HUSH
Hush has an impressive amount of releases for their wallets including Windows, Mac, Linux, and a newly released web wallet as well.
How to mine HUSH
One of the best things about Hush is its fair launch and ground-level opportunity for miners. The Hush team put together a fairly comprehensive starters guide on their forum. Since Hush leverages the Zcash codebase, it uses Equihash for its Proof-of-Work (POW) so there is already a lot of data and improvements out there on mining with this algorithm.
Conclusion
Ultimately, HUSH aims to be much much more than simply a Zcash “clone” through its consistent community focus, previously unavailable protocol-level security features, and secure messaging. The ability to link up with a decentralized exchange and asset issuance opens the door for building additional robust functionality and utility for users.
Hush lives up to its name, not only because it’s a quiet sleeping giant but also because it implores us to demand a higher standard of privacy built within our technology.
Never Miss Another Opportunity! Get hand selected news & info from our Crypto Experts so you can make educated, informed decisions that directly affect your crypto profits. Subscribe to CoinCentral free newsletter now.