TLDR
- Hackers are exploiting Ethereum’s EIP-7702 upgrade to steal WLFI tokens from World Liberty Financial holders
- The exploit involves pre-planting malicious smart contracts in victim wallets after private keys are compromised through phishing
- Multiple users report losing tokens, with some managing to save only 20% of their holdings in emergency transfers
- The attack occurs when users deposit ETH for gas fees, triggering automatic token theft by sweeper bots
- WLFI team warns against fake support messages and scam tokens targeting the launch
World Liberty Financial token holders are losing their WLFI holdings to hackers using a known phishing exploit. The attack leverages Ethereum’s recent EIP-7702 upgrade to drain tokens from compromised wallets.
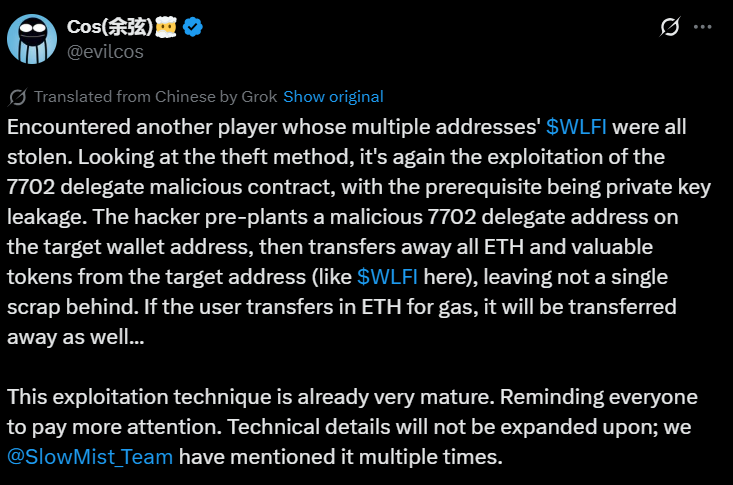
SlowMist founder Yu Xian identified the exploit method in social media posts. He explained that hackers are using the “classic EIP-7702” technique to target WLFI token holders across multiple wallet addresses.
The exploit takes advantage of Ethereum’s Pectra upgrade from May 2024. This update introduced EIP-7702, which allows external accounts to temporarily function like smart contract wallets.
The upgrade enables batch transactions and delegated execution rights. These features were designed to improve user experience on the Ethereum network.
However, hackers found ways to abuse these new capabilities. They compromise private keys through phishing attacks first.
Once they have the private keys, attackers pre-plant malicious smart contracts in victim wallets. The contracts remain dormant until users make deposits.
How the Attack Works
The theft occurs when users transfer ETH into their wallets for gas fees. As soon as the deposit arrives, the malicious contract activates automatically.
The pre-planted contract immediately transfers all tokens to hacker-controlled addresses. Users have no time to react or prevent the theft.
Xian described encountering a victim whose WLFI tokens were stolen from multiple addresses. All thefts followed the same pattern using the delegated malicious contract exploit.
World Liberty Financial began trading on Monday with 24.66 billion total tokens. The Donald Trump-backed project quickly became a target for various scam attempts.
One X user reported their friend’s tokens were drained after depositing ETH. Xian confirmed this matched the classic EIP-7702 phishing pattern.
Victims Share Their Experiences
WLFI forum users are reporting similar theft experiences. User hakanemiratlas said their wallet was compromised in October 2024.
They managed to save only 20% of their WLFI tokens through emergency transfers. The process involved racing against hackers while risking additional theft.
“Even sending ETH for gas fees felt dangerous, since it could have been stolen instantly,” they wrote. The remaining 80% of tokens remain trapped in the compromised wallet.
Another user named Anton explained why many holders face this problem. The WLFI presale requires using the same wallet that joined the whitelist.
Anton requested direct transfer options from the WLFI team. Without this feature, automated sweeper bots steal tokens immediately upon arrival.
The user warned that compromised wallets become unusable for any transactions. Any attempt to move funds triggers the malicious contract.
Security Solutions and Warnings
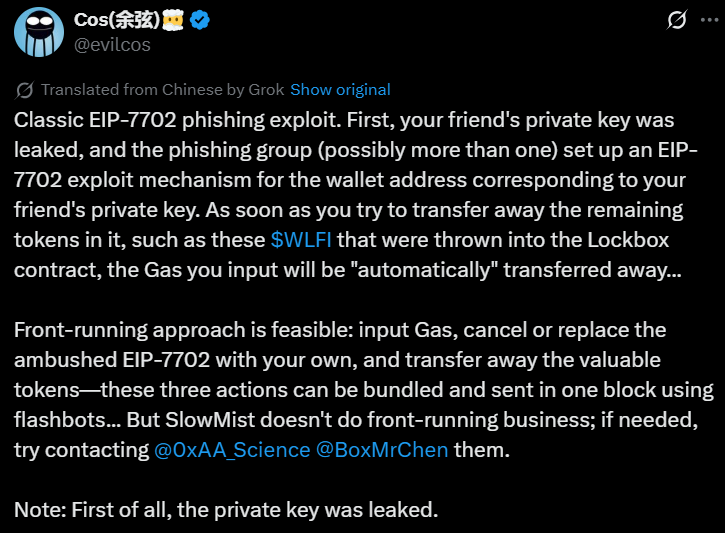
Xian suggested potential solutions for affected users. He recommended canceling or replacing the malicious EIP-7702 delegation with user-controlled contracts.
Transferring tokens away from compromised wallets offers another option. However, this requires successfully executing transactions before hackers can respond.
Analytics firm Bubblemaps identified multiple WLFI scam contracts. These “bundled clones” imitate legitimate crypto projects to deceive users.
The official WLFI team issued warnings about fake support contacts. They confirmed they never reach out through direct messages on any platform.
Users should only trust official email communications from verified domains. All direct messages claiming WLFI affiliation are fraudulent attempts.
The team emphasized checking email sender domains carefully before responding. Scammers often create similar-looking addresses to trick victims.
Multiple users report ongoing thefts as the exploit continues targeting WLFI holders.