- Why 2FA?
- User Preferences
- Best Types of 2FA
- Any 2FA is Better Than No 2FA
- Keep Your Backup Codes/Private Keys
- Conclusion
Why 2FA?
2FA stands for two-factor authentication, and it has quickly become a new cybersecurity standard across much of the internet, including cryptocurrency. In the early days of the internet, we relied on the humble password to protect our accounts. Over the years, however, it became clear that passwords are easy to guess or steal and more protection is necessary. This post looks at why 2FA rose to prominence and the best types of 2FA you should be using to protect your online accounts and crypto assets.
The basic idea behind 2FA is finding another way to confirm the user’s identity beyond a password. By now 2FA is everywhere. If you’ve ever entered a 6-digit PIN that a company texted or emailed you, then you’ve used two-factor authentication.
User Preferences
Increasing account security and introducing more hurdles for would be attackers is the name of the game. However, many users grow weary of these extra steps. It’s a common trope in cybersecurity that “users don’t want any more security than they think they need.” That is to say, most users understand why 2FA is important and they like 2FA. However, they want it to be as unobtrusive as possible.
The result is a system that could be highly secure, but in most cases, it sacrifices security in favor of user-friendliness. Many users believe that because they’ve enabled 2FA their account is now impenetrable. That’s simply not true. There are varying levels of effectiveness within 2FA.
Best Types of 2FA
The various types of 2FA provide varying levels of security. The best types of 2FA are the ones where the user controls all of the authentication process, without the use of a third party. The fact of the matter is that any time a middleman gets involved in the authentication process, that’s an opportunity for an attacker to insert themselves.
Let’s take a look at the worst and best types of 2FA:
Worst: SMS
Attackers have proven time and again that it’s easy to compromise text message 2FA. Usually, it involves the attackers calling the cellular service provider and tricking customer service into giving access to the account. Once in, the attackers can read incoming text messages to the target’s phone number. Intercepting an SMS 2FA code then gives attackers access to the account.
SMS is the least secure form of 2FA, but it’s also the most popular. Cryptocurrency exchanges and other service providers that offer SMS verification do so because it’s the quickest and easiest option for users. It also allows the company to ask for phone number information, gathering more data on their customers.
If you have the option to choose how you’d like to receive your 2FA codes, you should generally avoid SMS as it’s the least secure.
Less Bad: Email
Email is a slightly better option than SMS for authentication codes. This is because gaining access to your email is not as easy as calling up a customer service representative. However, email can still be attacked as it involves a third-party provider and your computer that can be compromised, including email forwarding schemes or screen readers.
Ideally, you’d want something that works more quickly and dynamically than email.
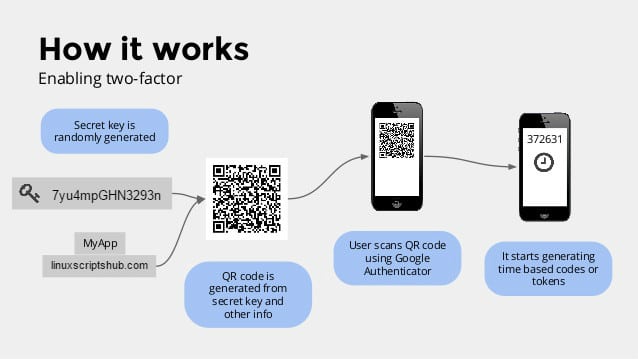
Good: Authenticator App
Authenticator apps on your smartphone are probably the best choice for most users. They involve codes that change every 30 seconds. This dynamic switching of the one-time code makes authenticator apps one of the best types of 2FA. Google Authenticator and Authy are two popular options for authenticator apps.
Most crypto service providers are on board with authenticator apps. Just simply scan the barcode on the service’s website and enter the dynamic code that appears in your app.
Best: FIDO Hardware Keys
Like hardware wallets, hardware authentication keys turn the problem of authenticating into a physical device. You can plug a device like a Yubikey into your computer’s USB port to access your favorite websites. This is by far the most secure since an attacker would need to have your physical hardware key to get access. However, it’s the most cumbersome option as well, since you always have to keep the key with you.
Any 2FA is Better Than No 2FA
The best types of 2FA make it much more difficult for attackers to get access to your account. However, any type of 2FA adds another layer of security beyond your password. As such, if a site offers 2FA of any kind, you should enable it. Taking account security beyond the realm of passwords is why 2FA is so important and growing so quickly.
[thrive_leads id=’5219′]
Keep Your Backup Codes/Private Keys
If you lose access to your phone or email, then you won’t be able to receive 2FA authentication codes. For that reason, it’s always important that you keep copies of your private keys and backup codes somewhere safe. That way, you’ll be able to restore access when you get a new phone.
It should go without saying, but never share your private keys with anyone. Similarly, don’t give anyone access to your cellular account or authenticator codes. Common scams include a customer service representative calling you and claiming to send you a code which you’re then supposed to read back to them. Once you realize the friendly customer service rep was really a scammer, it’s too late. Don’t share codes or passwords over the phone, ever!
Conclusion
Everyone should set up 2FA for all their online services, not just cryptocurrencies but every service you use. It introduces a new level of access control that makes it harder for attackers to gain access to your accounts. Some forms of 2FA are better than others, but any 2FA is better than none. The best types of 2FA make it easy to find your codes while making them dynamic and secure from third-party interference. These advances in usability and security are why 2FA is growing in popularity and adoption across the crypto industry and the internet in general.
Never Miss Another Opportunity! Get hand selected news & info from our Crypto Experts so you can make educated, informed decisions that directly affect your crypto profits. Subscribe to CoinCentral free newsletter now.