Blockchain cryptography is at the very heart of what keeps cryptocurrencies and other digital assets safe from hackers and other cyber-attacks. Public key encryption provides each user with a public and private key, which are extremely difficult to guess through brute-force attacks, at least using today’s computing resources. However, developments in quantum computing will make brute-force attacks far easier in the future.
Here, we will take an in-depth look at how a quantum computer could successfully attack existing blockchain cryptography. Considering some projects are already making headway, we’ll also look at how blockchains can be secured against quantum machines.
How Can a Quantum Computer Break Blockchain Cryptography?
Blockchain uses public key encryption, where each user is given a public and private key to secure their digital assets. These keys are generated using a cryptographic method called prime number factorization, which is the backbone of all modern cryptography.
The mathematical principle behind prime number factorization is that any number, no matter how large, can be produced by multiplying prime numbers. It’s relatively easy to produce any number using prime numbers. However, it’s vastly more difficult to reverse the process and work out which prime numbers were multiplied to produce a particular value once the numbers become large. This reversal is called prime number factorization.
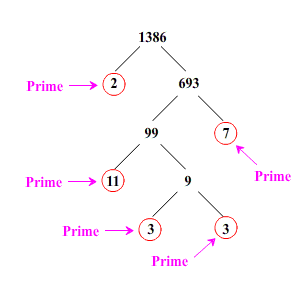
Key Encryption and Prime Number Factorization
Blockchain cryptography relies on prime number factorization for linking the public and private key. The prime number factors of the public key are what form the private key. Because today’s computers, even using the advantages of networks, cannot factor the private key, our digital assets can remain secure against attackers.
For example, in 2009, researchers used a network of computers to try and factor a number 232 digits long. It took the equivalent of 2,000 years for a single computer launching such an attack. Computer security specialists nevertheless thought this was an unacceptable risk. Thus, current encryption standards use prime numbers that are 309 digits long.
Quantum computers are capable of performing many more thousands of calculations per second than today’s computers, even accounting for the network effect. Quantum machines are still in a relatively early stage of development. However, its thought that over the next decade, quantum computers will become sufficiently powerful to break existing blockchain cryptography.

Therefore, one of the challenges for the blockchain developer community is ensuring that existing blockchains are resilient enough to withstand attacks from tomorrows quantum computers.
The Specific Threat of Quantum Computing to Blockchain
Because all current cybersecurity relies on encryption using prime number factorization, the advent of quantum computing isn’t just a threat to blockchain encryption. It has implications across the whole of the internet and all connected computers. However, centralized entities control pretty much all websites and networks outside of blockchain. Therefore, it isn’t a significant problem to implement an upgrade across the network or website.
On the other hand, decentralized networks control blockchains. Decentralization means that every computer on the network has to agree to upgrade at the same time for the upgrade to become active. Not only that but because the quantum threat to blockchain cryptography is specific to the public and private keys, then all wallets will need to upgrade to the new software to ensure quantum resistance.
[thrive_leads id=’5219′]
The Worst Bear Market in Future History?
Satoshi Nakamoto is thought to own around a million Bitcoins, not to mention his fortunes from the many Bitcoin hard forks over the years. If the Bitcoin network pushes through an upgrade to ensure quantum resistance, and Satoshi doesn’t upgrade his BTC wallets to the new protocol, his wallets become vulnerable to the quantum threat. So, even if all other holders of BTC upgrade their wallets, a quantum attack could still see Satoshi’s one million BTC stolen and sold off onto the market in one fell swoop.
Even worse though, it’s not just whales that are at risk. After all, anyone consciously sitting on crypto-wealth will be eager to upgrade as soon as possible. However, it’s thought that around four million BTC are lost due to their users losing their private keys. Someone stealing and then selling this volume of crypto in a short space of time could have a devastating effect on the markets.
Therefore, developing quantum resistant blockchain cryptography is not necessarily the problem. The implementation across thousands or even millions of wallets becomes the real challenge.
Securing Blockchain Cryptography against the Quantum Threat
Most people still think the quantum threat is several years away, perhaps even more than a decade. However, the above scenario illustrates why it’s vital that developments in blockchain cryptography already start to consider quantum resistance as a precautionary measure.
One-time Signatures with Cryptographic Hashing
Quantum Resistant Ledger (QRL) is not one of the biggest blockchain projects out there. However, its sole use case is in ensuring quantum resistant blockchain cryptography. The project works from a principle that prediction timelines about advancements in quantum technology may be fallible. For this reason, we should already start preparing for the eventuality that quantum developments may arrive sooner than we think.
The QRL blockchain completely does away with prime number factorization for blockchain cryptography. Instead, it makes use of Extended Merkle Signature Schemes (XMSS), which is a complex model. However, in principle, it involves generating key pairs using cryptographic hashing. This is the same concept as hashing a block in a blockchain to protect the contents.
These key pairs are for one-time use only and are aggregated together using a Merkle tree. By using hash-based blockchain cryptography rather than prime number factorization, the signatures become far more complicated to brute-force. This hashing makes them resistant to quantum attacks.
The Nexus blockchain uses another mechanism when handling transactions, called signature chains. Nexus hashes the public key so although it’s visible on the blockchain, it isn’t readable.
The public key hash then generates a one-time private key as an authorization signature for the transaction. Afterwards, the wallet automatically creates a new public/private key pair for the next transaction, along with a sending or receiving address for the current transaction. In this way, the transaction keys are separate from the address, making it more secure against quantum attacks. While this is not yet 100 percent quantum-proof, Nexus plans future upgrades to its infrastructure that should ensure a better degree of quantum resistance.
Conclusion
Despite that the threat may still be some way off, blockchain cryptography faces some unique challenges from quantum computing. The developer community is very much aware of the threat. Hence, the introduction of innovative solutions such as the ones listed here. Implementing these kinds of solutions will prove to the most challenging part of quantum-proofing the major blockchains such as Bitcoin and Ethereum.
However, the blockchain developer community is nothing if not creative. It will be fascinating to see some of the ideas coming out of the quantum challenge. Furthermore, find out which of those ideas will ultimately evolve into the most resilient solutions.
Featured image courtesy of Pixabay
Never Miss Another Opportunity! Get hand selected news & info from our Crypto Experts so you can make educated, informed decisions that directly affect your crypto profits. Subscribe to CoinCentral free newsletter now.