Distributed computing, mechanism design, and cryptography algorithms form the holy trinity of blockchain technology. Distributed computing utilizes a decentralized network of computers and existed before blockchains in the form of torrenting networks.
However, torrenting sites had no means of governing the behavior of participants, which is where mechanism design enters into blockchain. It provides the incentive for network participants to work for the good of the network.
Cryptography is what serves as security for protecting those incentives. The seminal Bitcoin white paper explained how these three scientific principles could play together to form a secure, peer-to-peer exchange of value that would eliminate the need for a third party in financial transactions.
While each of these principles is deserving of its own explainer, this article will focus on cryptography, and how encryption algorithms serve blockchains.
A Brief History of Cryptography
Cryptography in some form has been around since the time of ancient Egypt. Before the age of computing, it meant using a simple cryptography algorithm called a cipher to transmit messages. One of the most often-cited is the Caesar cipher, used by Julius Caesar to communicate with his generals in the Roman Empire. The Caesar cipher substituted each letter of the message by the letter that comes three places after it in the alphabet, so A becomes D, B becomes E and so forth. As long as the system used in generating the ciphertext remains secret, the message could also remain private.

Later on, in the 16th century, Vigenere introduced the concept of an encryption key to cryptography algorithms, which could decrypt coded messages. Using the Vigenere cipher, the message text was transcribed into a single keyword that is repeated until it matches the character length of the original message. This keyword then generates the ciphertext using a table.
The critical development here is that security of messages transmitted using a Vigener cipher depended on the secrecy of the key, not the system itself.
20th Century Developments
The problem with these kinds of codes is that they are easily breakable by analyzing letter frequency. The Germans used the Enigma Machine extensively during World War 2 because it was able to generate ciphertexts that could not be broken by analyzing letter frequency.
The machine used a system of multiple rotors to generate the ciphertext. So the letter “e” in the original message would correspond to a range of different letters in the cipher text. The key was the initial setting of the rotors.

Although the Germans thought that the code was unbreakable, Enigma was cracked by the Polish as early as 1932. Cryptographers working for the British military in Bletchley Park, including the now-legendary Alan Turing himself, later found a way to figure out the daily keys used by the Germans.
The Dawn of Computing
Post-war, demands for encryption in the business and commercial space increased as a means of protecting corporate secrets. During the 1970’s, IBM developed the Data Encryption Standard (DES) cryptography algorithm. However, it used a small encryption key. As the age of computing dawned, it became easy to brute-force DES, and hence there was a demand for an update. The Advanced Encryption Standard adopted in 2000.
Although many people may not be conscious of it, encryption is now part of daily life. Email and text messaging, passwords, and SSL layers on websites all involve the use of encryption. It also forms the backbone of cryptocurrency. There are many different types of cryptography algorithms covering various use cases, lots of them already obsolete. However, the use of cryptography in blockchain comprises digital signatures and hashing.
Digital Signatures
Cryptocurrency payments require a digital signature, in the form of a private key. When someone enters their private key against a payment transaction, this encrypts the transaction. When the payment reaches its destination, the recipient can decrypt the transaction using the public key of the sender.
This is known as asymmetric cryptography, as it depends on a pair of keys linked together by cryptography. It is more secure than symmetric cryptography, where both sender and recipient use the same key. In this case, the key itself must also be transmitted along with the payment, which means an additional layer of security would be needed to protect the key.
Hashing
Blockchains are also dependent on hashing. Hashing is a cryptographic method of converting any kind of data into a string of characters. As well as providing security through encryption, hashing creates a more efficient store of data, as the hash is of a fixed size.
Characteristics of Hashing Cryptography Algorithms
A cryptographic hashing algorithm must fulfill specific criteria to be effective:
- The same input must always generate the same output. Regardless of how many times you put the data through the hashing algorithm, it must consistently produce the same hash with identical characters in the string
- The input cannot be deduced or calculated using the output. There should be no way to reverse the hashing process to see the original data set
- Any change in the input must produce an entirely different output. Even changing the case of one character in a data set should create a hash that is significantly different
- The hash should be of a fixed number of characters, regardless the size or type of data used as an input
- Creating the hash should be a fast process that doesn’t make heavy use of computing power.
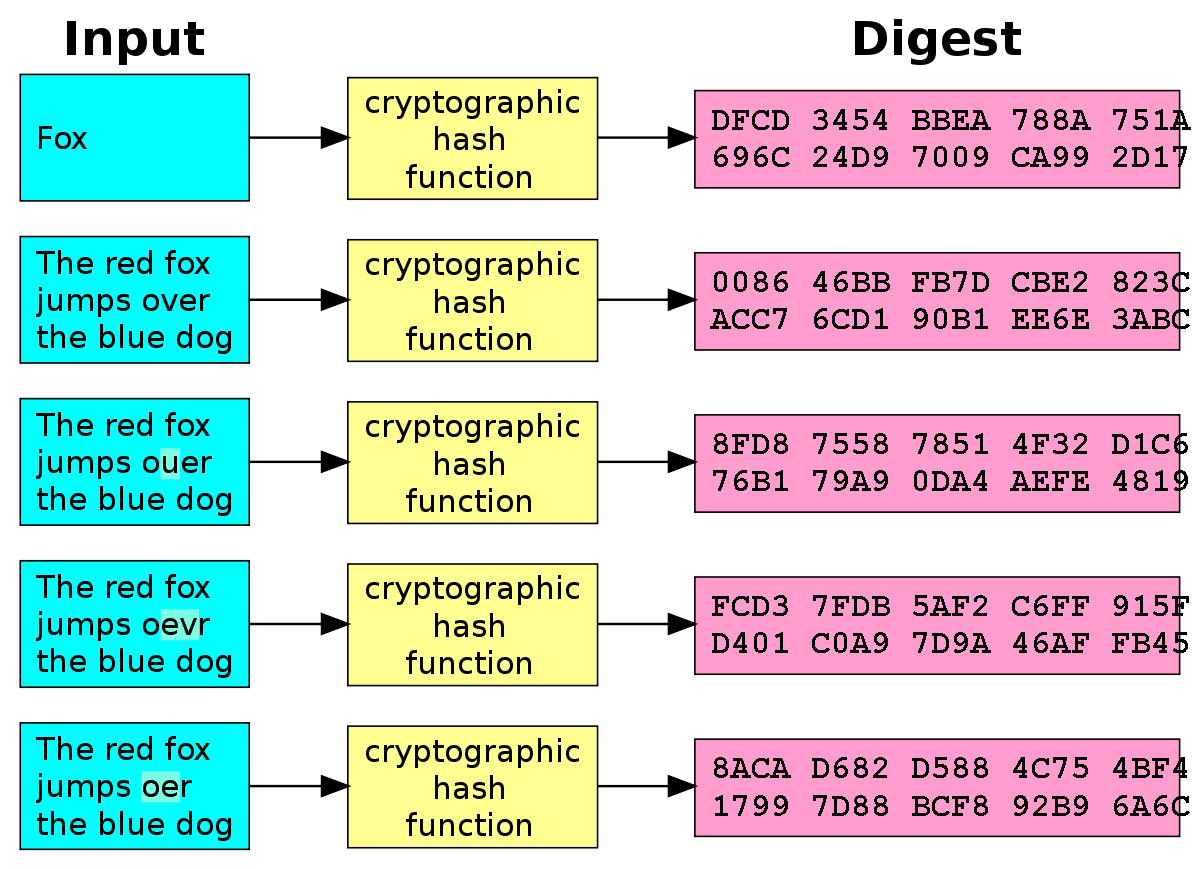
How Does Hashing Work?
Blockchains hash each transaction before bundling them together into blocks. Hash pointers link each block to its predecessor, by holding a hash of the data in the previous block. Because each block links to its predecessor, data in the blockchain is immutable. The hashing function means that a change in any transaction will produce an entirely different hash, which will alter the hashes of all subsequent blocks. To propagate a change across the blockchain, 51% of the network would have to agree to it. Hence, the term “51% attack”.
Different blockchains use different cryptography algorithms. The Bitcoin blockchain uses the SHA256 algorithm, which produces a 32-byte hash. Dogecoin and Litecoin both use Scrypt, which is one of the faster and lighter cryptography algorithms.
Cryptography is a complex and detailed science, that reaches way beyond the scope of just blockchain. There is plenty of further reading available on cryptography, especially for the more scientifically or mathematically inclined, it is a fascinating subject with much to explore.
[thrive_leads id=’5219′]