When setting up a distributed computing network, there are different types of distributed system architecture that may be deployed. In this article, we take a deeper look at the types of distributed system architecture, with a specific focus on the peer-to-peer distributed system architecture of blockchain.
Types of Distributed System Architecture
Client-Server Model
Applications like email or networked printers typically use the client-server architecture. Essentially, providers (called servers) and requestors (called clients) have different roles. The server handles all of the processing, data management, and computing requirements, which are available on-demand to the client. If a database entry changes, the client doesn’t necessarily need to do anything. Only the data on the server needs to be changed.
The server doesn’t have to be a single device in this model; it could be multiple servers performing similar tasks to distribute the workload. The model refers to the role of the client and server, rather than the specific hardware.
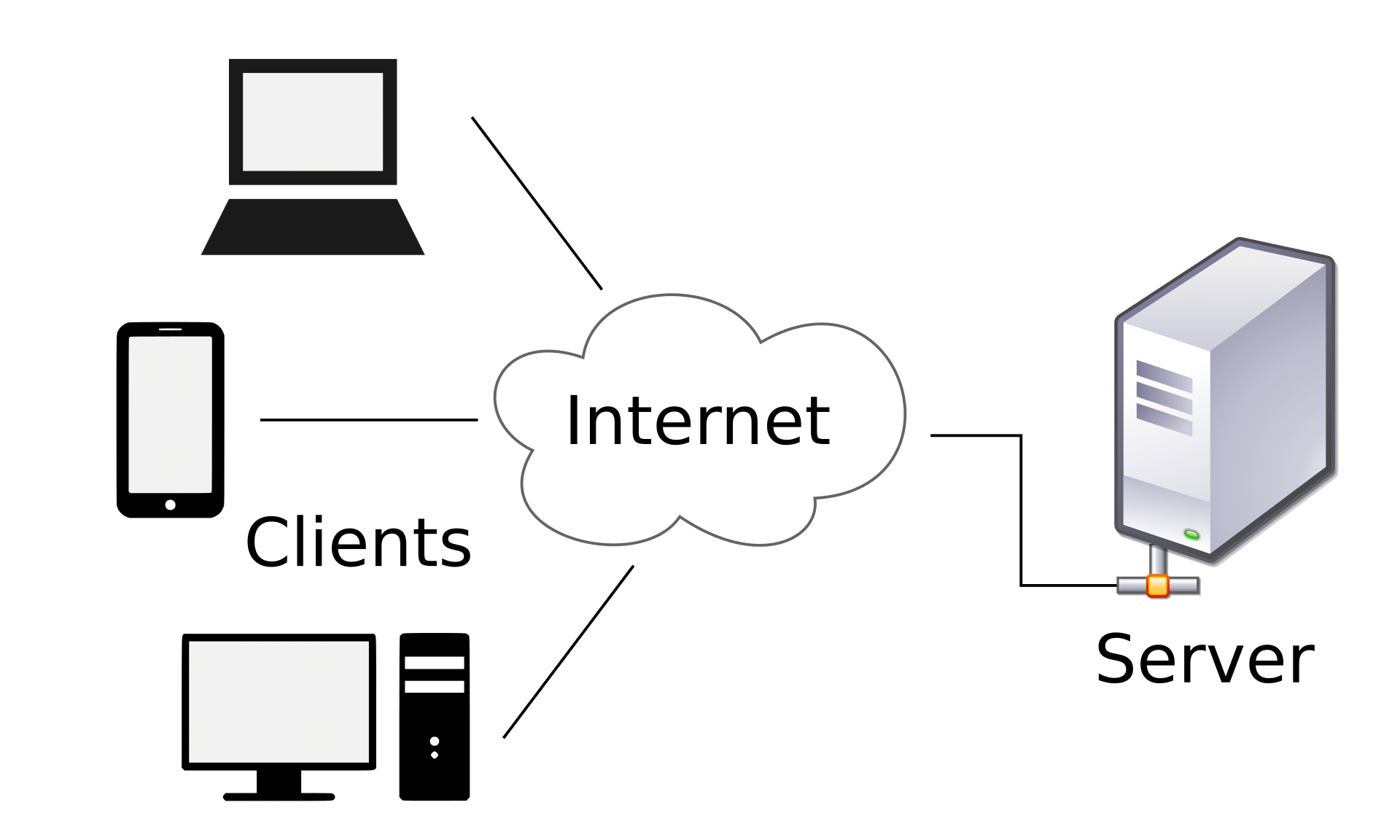
We use client-server interactions every day, each time we use a laptop or smartphone to surf the web, use social media apps, play mobile games, or watch a movie on Netflix. Client-server distributed system architecture is what we refer to when we talk about “centralized” computer systems, in contrast to blockchain as a decentralized distributed system architecture.
While this is a simple explanation, there are different types of client-server architecture, such as three-tier. This model involves separating the server running the application itself from the server housing the data behind the application. There are others, but as they aren’t relevant to blockchain, we won’t analyze them all here.
[thrive_leads id=’5219′]
Peer-To-Peer Model
A peer-to-peer (P2P) distributed system architecture doesn’t have any specific clients or servers. A P2P network is a distributed system of machines called nodes. All nodes can perform the role of client and server either concurrently or at different points in time. The model is inherent in the name itself — in a P2P network, each machine is an equal peer, rather than being a client or a server.
P2P networks become popular after the release of file-sharing services like the music-sharing site Napster. The idea of P2P gained a kind of cult status because systems could operate independently of any centralized control. Today, outside of blockchain, file sharing protocol BitTorrent is probably the biggest and most recognizable name associated with P2P networks.
Unstructured vs. Structured Networks
Based on how the nodes link to one another, and how data is indexed and discovered, P2P networks are classified as structured or unstructured. In an unstructured system, nodes simply form random connections to one another. Unstructured networks are easy to build and scale up or down.

However, because they are unstructured, it makes indexing much more difficult. If a node wants to find a particular piece of data or another node, it must flood the network to reach as many nodes as possible that may be a potential target for the search. This uses more network power, as all nodes must process all requests. Moreover, if the data is rare, it may not be found if all nodes on the network are unable to process all requests. Examples of unstructured networks include Kazaa and Limewire.
On the other hand, locating any data on a structured network is easy. Structured networks use a distributed hash table to identify which peers are holding which files and versions of files. Chord is one example of a structured P2P network.
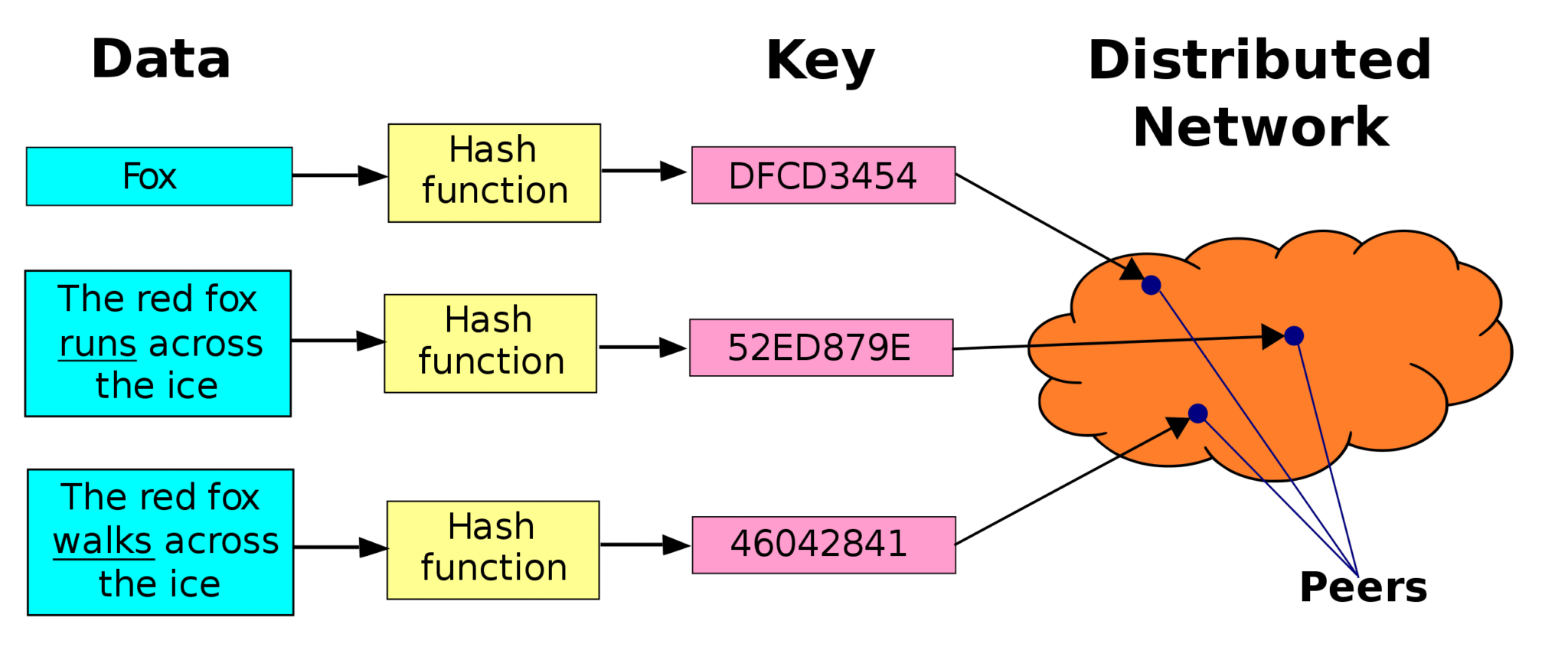
Why Blockchain is Special
As a pure model for distributed system architecture, P2P networks have various benefits and challenges. The key advantage is resilience to downtime because there is no central point of failure.
However, because nodes in a P2P network are acting as both client and server, they are more vulnerable to attacks. Such attacks may include denial of service or distribution of malware or corrupted data. One study found that 15 percent of half a million files downloaded from Kazaa were infected with 52 different viruses.
While blockchains are not 100 percent incorruptible, Satoshi came up with an ingenious solution to the vulnerability problem when he wrote the Bitcoin white paper. By introducing a consensus protocol, all nodes on the Bitcoin network must agree that a transaction is valid. The use of game theory has each node competing to mine the next block.
Successfully mining the next block comes with a reward, providing node operators with an incentive to keep the network clean. Provided 51 percent or more of the node operators work in tandem to keep competing for the next block reward, the blockchain continues running free of attacks.
Conclusion
Of course, there are other elements to Bitcoin, such as the use of hashing and cryptographic signatures, that create the store of digital value. However, the solution invented by Satoshi for overcoming the inherent weaknesses in a P2P distributed system architecture remains one of the most compelling and innovative components of blockchain.
Since the inception of Bitcoin, many others have come up with inventive developments based on Satoshi’s idea. Those developments continue to this day. Blockchain represents a revolutionary step in distributed system architecture. Furthermore, the technology will still evolve for many more years to come.
Featured image courtesy of Pixabay