Privacy and anonymity oriented coins are becoming a pervasive and often contentious topic. As a result, many figures in the media and government have cast a distrustful eye on such protocols fearing a new medium for illicit and illegal activity. Meanwhile, freedom lovers applaud these new developments as an unprecedented evolution of not only technology but stateless financial freedom.
A solid argument I came across in favor of privacy was from the Zerocash white paper which stated:
“Privacy guarantees are designed to benefit legitimate users who do not want their financial details made public. There is a concern, as always, that decentralized anonymous payments will facilitate the laundering of ill-gotten funds by criminal users….however [Privacy coins] barely affects the status quo for criminal users, who already have strong incentives to hide their activity, while it provides notable benefits to legitimate users.”
Why do we need privacy?
Bitcoin utilizes cryptography to disguise identities and has a transparent public ledger. On one hand, this is an amazing construct but we need to consider the implications. Public wallets are viewable by anyone and include not only the balance of the wallet but also how much money has been received and paid out (including the public wallet addresses of senders and receivers).
Sure, this might be great for a non-profit or other publicly transparent entity…but do we really want anyone and everyone to see what we have and who we send to?
Businesses may have trade secrets or a list of clients and suppliers they want hidden. As a user, a safety concern arises as hackers could easily find and target large holders.
Introducing privacy coins.
These coins are meant to help give users a degree of anonymity in a robust and decentralized manner.
This guide highlights the technology, teams, and purpose between privacy coins including Monero, Zcash, Dash, Verge, PIVX, and Hush.
While there are other coins tackling these same use cases, we have opted to narrow down to the most popular coins based on the technology, market capitalization, adoption, and brand awareness.
Monero
Originally launched in April 2014 as BitMonero, Monero (symbol XMR), means money in Esperanto. Monero is a fork of Bytecoin and is a secure private untraceable currency.
A brief history from their website shares how we got to the current team: “The founder, thankful_for_today, proposed some controversial changes that the community disagreed with. A fallout ensued, and the Monero Core Team forked the project with the community following this new Core Team. This Core Team has provided oversight since.”
Monero leverages the CryptoNote technology as well as Ring Signatures, Ring Confidential Transactions and Stealth Addresses.
What is CryptoNote?
CryptoNote is an open-sourced protocol that allows for increased privacy in cryptocurrency transactions. Most traditional cryptocurrencies use unchanging signatures to verify transfers, while CryptoNote uses ring signature.
Ring Signatures: Cloaking the Sender
Ring Signatures are a type digital signature in which a group of signers is brought together to sign a transaction forming a ring. This is similar to a joint bank account but with the actual signer being unknown.
The actual sender generates a one-time spend key and the recipient is the only party that can detect and spend the funds based on that key. Since all outputs are unlinkable, the privacy of the recipient is ensured.
How double spending is prevented
If the outputs of the sender are prevented from being seen, what would prevent the outputs from being spent twice? Also, how might one verify a transaction occurred? Well, time to meet key images.
A key image is a cryptographic key derived from an output being spent that is made part of every ring signature transaction. There can exist only one key image for each output on the blockchain.
Based on its cryptographic properties it’s not possible to determine which output created which key image. A list of previously generated key images is maintained in blockchain allowing miners to verify that outputs weren’t spent twice.
Ultimately key images allow outputs to be authenticated without connecting it to the wallet address.
Ring Confidential Transactions (RCT): Masking Amounts of Funds
As of January 2017 Ring Confidential Transactions were activated optionally within the protocol. Now, it is a mandatory part of the protocol as of September 2017.
Prior to RingCT, transactions had to be split into multiple amounts. (E.g. If you sent 10 monero, it would be chunked into amounts like 2, 1.5, 3 and 3.5) The downside is that the amounts could still be seen regardless of being broken up.
Today with RingCT newly created monero first resides in outputs that have visible amounts. However, when the new monero is transferred for the first time, RingCT masked amounts are generated.
For example, if John has 12 Monero and sends 2 to Bill, John will send 12 and receive 10 back (the 12 – 2 for Bill) as “change”. To prove that Monero has not been fraudulently fabricated in the transaction, the sum of the transaction inputs must equal the sum of outputs
Due to cryptographic properties of RingCT, John is required to commit to the amount of the output revealing just enough information for the network (miners) to confirm the transaction while not publicly disclosing the total amount she is spending.
Although commits look like random numbers, miners can confirm the amount being sent is the same as a number of funds available.
Stealth Addresses: Hiding the receiver
In every transaction, a stealth address (aka a one-time public key) is automatically generated for the transaction to indicate who can spend funds in a later transaction.
An outside observer cannot tell if funds are moving from one to another or link wallet addresses together.
The funds going to the receiver are not connected with their wallet, however, the one-time key (stealth address) can be validated by a 3rd party to prove the transaction occurred.
The receiver can find the output destined for them by scanning the blockchain with their wallets private view key. Once the output is detected and retrieved by the wallet, the receiver would be able to calculate a one-time private key that corresponds to the sender’s one-time public key.
The receiver could then spend the relevant output with their wallets spend key. This whole process all occurs without having the receivers wallet publicly linked to any transaction.
Needless to say, Monero is a force to be reckoned with not only with the solidarity of the community and developers but a pretty unique technology that tackles a lot of previously unsolved problems with other cryptocurrencies.
Dash
Dash (formerly known as Darkcoin and XCoin) is an open source peer-to-peer cryptocurrency originally forked from Bitcoin. Dash offers the same features as Bitcoin but has improved capabilities, including instant and private transactions.
Originally founded in January of 2014, Dash uses a two-tier architecture to power its network. The first tier consists of miners who secure the network and write transactions to the blockchain. The second tier consists of masternodes who handle the instant and private transaction sending and decentralized governance.
The main features of Dash include:
- InstantSend – Immediate transactions with ability to handle large volumes
- PrivateSend – A coin mixing service based on a decentralized CoinJoin implementation
- Decentralized Governance by Blockchain (DGBB) – A mechanism for management of future funding and development through a self-governing community
InstantSend
Originally called InstantX and rebranded in June 2016 as InstantSend, this component facilitates near-instant transactions. Using this system, inputs can be locked to specific transactions and verified by the masternode network. In addition, it could potentially compete with Bitcoin and even Visa’s throughput with capabilities 500-1000 transaction per second.
PrivateSend
PrivateSend is decentralized coin-mixing service based on CoinJoin. This includes using masternodes in place of a single gateway, chaining by mixing with multiple masternodes, restricting the mixing to only accept certain denominations (e.g.: 0.01 DASH, 0.1 DASH, 1 DASH, and 10 DASH, etc.)
The main problem with CoinJoin is that users cannot negotiate transactions within the Bitcoin protocol forcing users to send their funds outside of the Bitcoin network to centralized services.
Dash aimed to create a decentralized CoinJoin construct within the protocol through full nodes who handle the mixing service internally between randomly selected nodes.
One critique of this approach is a Sybil attack where malicious parties create thousands of nodes to control a majority % of the network. This could lead to centralized control of user transactions ultimately deanonymizing them.
To remedy this, Dash created a collateralized node approach called Masternodes requiring 1000 Dash to run a Masternode. In addition. Masternodes are rewarded (similar to miners) for providing the mixing service honestly.
Decentralized Governance (DGBB)
Dash is a decentralized autonomous organization powered by a Sybil proof decentralized governance and funding system called Decentralized Governance by Blockchain (DGBB). Also referred to as the “treasury system”, the DGBB is a consensus mechanism on network development and funding of the Dash ecosystem. 10% of block rewards go to this treasury.
In addition, each masternode operator receives one vote. MNs vote on proposals submitted through dash.org forums and other community-driven websites like DashCentral. Proposal submitters typically provide multiple drafts and lobby for community support before sharing their project with the network for a vote. After the proposal is accepted, the network automatically pays out the funds in the next super block, which occurs monthly.
Dash has evolved greatly since its inception as Darkcoin and ultimately has proven to be a player by surviving and building upon the original code and project. In addition, by tackling problems that were unsolved by Bitcoin it has truly added functionality and reduced friction to the ecosystem as a whole.
ZCash
ZeroCoin – The Catalyst for ZCash
Before we jump into Zcash, it’s important to understand the protocol that preceded it.
Zerocoin is a cryptographic currency protocol created by Ian Miers, Christina Garman, Matthew Green, and Aviel D. Rubin in 2013. The next iteration was called Zerocash which was an improvement on the protocol which included the original team and Eran Tromer, and Madars Virza in 2014.
Bitcoin operates in a transparent manner by broadcasting and verifying payment transactions on a public ledger. Zerocash differs in how these payment transactions are assembled and then verified, ultimately providing increased anonymity to the user.
It’s interesting to note that all of the scientists behind Zerocash are Zcash team members indicating this protocol will have support from the founders. In addition, they have such noteworthy investors as Roger Ver and Erik Voorhees.
ZCash – The First Widespread Application of Zerocash
Zcash is an implementation of the Zerocash protocol based on zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge). ZEC is the currency code for the Zcash currency and ⓩ is the currency symbol.
A zero-knowledge protocol is a way for one party to prove to a different party that a given statement is true, without conveying anything other than the statement is indeed true.
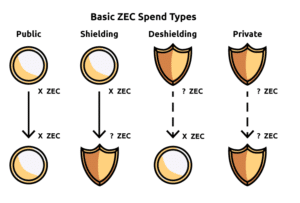
Zcash spend types
Funds in Zcash are either transparent (public) or shielded. The transparent value is the same as Bitcoin and has the same privacy features. Shielded value leverages notes which detail the amount and include a paying key which is part of the payment address and is a destination to which notes can be sent. This is connected with a private key that can spend notes sent to the address also called a spending key
A payment address includes two public keys: a paying key associated with the notes sent to the address and a transmission key which operates similarly to viewing key, only accessible by the holder of the related private key.
In short, a sender can send encrypted output notes on the blockchain to a receiver who uses the transmission (viewing) key to scan the blockchain for notes addressed to them and then decrypt those notes.
The core privacy characteristics of Zcash is when a note is spent, the spender proves a commitment for it had been revealed, without revealing which one. This means a spent note cannot be connected to the transaction in which it was created.
Zcash is one of those interesting projects that, although forked from Bitcoin, has incorporated and innovated some truly original technology which is not always the case with various “coins” hitting the market. With such legendary investors as Erik Voorhees and even interest from JP Morgan, Zcash is another up and coming powerhouse.
Hush
Hush is a private implementation of the Zerocash protocol forked from Zcash.
Hush has a trusted setup following the same methodology as the Zcash team which included a ceremonial burning of private keys which could access the network.
What’s the difference between Hush and ZCash?
As stated on the Hush bitcointalk announcement: “The on-chain assets that ZcashCo is working on to Zcash proper are not as powerful as counterparty assets, and they are not looking at directly adding the EVM to Zcash. The Zclassic and Zen development teams are currently in flux and while some of the promised features of ZEN are similar to those for HUSH, we believe we have and will continue to have a better track record of sipping releases.”
Hush and its team while sharing almost exact similarities with Zcash, have made an effort to fill in gaps that aren’t going to be filled for sure as well as making an inclusive and fair distribution of tokens for early birds who may have missed the Zcash boat early on. As a result, Hush is one to keep on the radar for the future.
PIVX
Private Instant Verified Transaction aka PIVX, is a decentralized open-source privacy cryptocurrency launched on February 1, 2016, as Darknet (DNET) before it was professionally re-branded to PIVX. PIVX runs on the Blackcoin PoS 2.0 protocol and is based on a Bitcoin fork (same as Dash).
The main difference between PIVX and Dash is that PIVX is 100% Proof of Stake. This means PIVX doesn’t rely on miners, instead rewarding holders through a Proof of Stake (POS) mechanism. This shift also puts more power in the hands of the Masternodes who verify transactions instead of the miners.
Another difference is the seesaw reward mechanism which PIVX uses to distribute block rewards. 90% of rewards go to Masternodes and Proof of stake nodes with 10% going to community projects.
Similar to HUSH, PIVX also provides a fresh and ground floor opportunities for new people who felt that they may have missed the Dash train. Leveraging the proven tech of Dash with their own tweaks and community support makes PIVX a solid player in the privacy space.
Verge
Verge is a privacy cryptocurrency focused on communication through protocols like I2p and Tor which have supported integrations with the platform with Android support as well.
Verge has 5 Proof-of-Work algorithms that run on its blockchain including Scrypt, X17, Lyra2rev2, myr-groestl and blake2s. Each algorithm has a 30-second block target block time. The difficulty is influenced only by the algorithms hash rate. This allows improved security and protection against 51% attacks.
Other noteworthy features include P2P transaction support for Telegram and Discord which is currently in development and slated to be released soon. With Telegram clocking 100 million users and Discord with 40, there is quite an audience they will be in front of.
Finally, there is future development to incorporate Rootstock (RSK): “RSK, is a two-way pegged sidechain that grafts smart contract functionality onto the Verge network. It also introduces an off-chain protocol for near-instant payments. RSK is an independent blockchain that does not have its own token, it instead relies on existing tokens (such as Verge). RSK is able to do this by pegging (or matching) its smart token to Verge, so that the value of an RSK token is exactly that of a Verge token. Users have the capabilities to freely move their tokens back and forth between the two chains.”
While being more of an integrator of various pre-existing constructs such as I2p and Tor as well as the Discord/Telegram and Rootstock incorporations tell me that Verge wants their stuff to work and work well. With a focus on communications and channels already used by their target market, this privacy token is going to keep the industry on its toes by offering a quality product.
Takeaways
We hope you enjoyed this journey into Crypto. As you can see, the world of privacy cryptocurrencies is very complex with a variety of underlying technology and use cases.
Keep in mind that although many Coins share similar approaches and characteristics, they are not by any means “the same”. Even forks and variations to the same code bases can be cloned, tweaked and modified to a developer’s heart’s content creating vastly different implementations from the original.
These tweaks and mods are often based on not just new ideas of how to do things but new scaling approaches that might not work on the original network the project was derived from. (As was the case with Zcash and Dash relative to Bitcoin)
This is why each coin especially the ones mentioned above are continuously innovating and finding ways to maintain their competitive edge and unique value propositions. Only time will tell who is going to win this battle.
Never Miss Another Opportunity! Get hand selected news & info from our Crypto Experts so you can make educated, informed decisions that directly affect your crypto profits. Subscribe to CoinCentral free newsletter now.