- Building Blocks with Nonces
- Relation to Mining Difficulty
- Why the Adjustment Matters
- Protection by Secure Hash Algorithms
- Value of Proof of Work
The nonce is a central part of the proof of work (PoW) mining algorithm for blockchains and cryptocurrencies like Bitcoin. Miners compete with each other to find a nonce that produces a hash with a value lower than or equal to that set by the network difficulty. If a miner finds such a nonce, called a golden nonce, then they win the right to add that block to the blockchain and receive the block reward.
The nonce is a random, one-time, whole number. Miners test and discard millions of nonces every second. They are hoping to produce a hash value that meets the target and so win the block reward. This is what happens during PoW mining at the most basic level, although, there is a lot more to it. Here, we are going to explore the entire purpose of the nonce throughout the mining process.
Building Blocks with Nonces
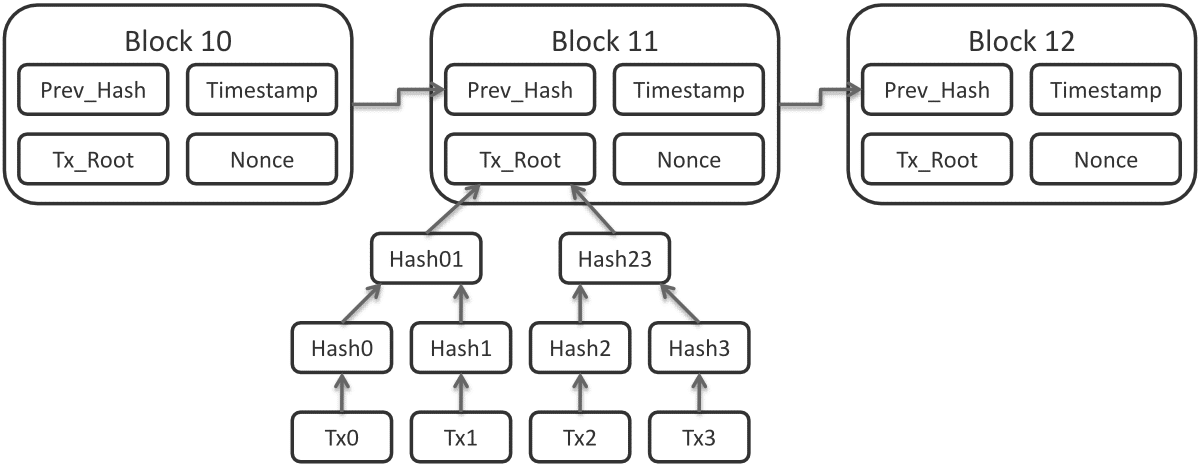
The nonce is a 32-bit number. It stays in the block header along with other key data, such as the difficulty target and timestamp. When miners build blocks, they randomly choose a nonce and input it into the block header, creating a new block header hash.
The hash is a 256-bit number and has to start with a huge number of zeros, i.e. have an incredibly small value. If it does not have the sufficient number of zeros, then the miner discards the hash and tries a new nonce. This process is repeated until a miner discovers a nonce that produces a hash with a value less than or equal than that set by the difficulty.
The 32-bit size of the nonce means that there are four billion possible combinations. Although technically, it is much higher due to something called the extra nonce. This is additional space for a longer nonce, meaning you can have tens of billions of combinations.
The nonce is the only parameter that the miner changes, all others remaining static. If the miner finds the golden nonce they add that block to the blockchain and receive the block reward. Currently, there is no way to speed up the process of finding the correct nonce. This means miners are just operating in trial and error until they find a golden nonce. This process is what constitutes the work, in proof of work.
Relation to Mining Difficulty
As we have said, the miner is trying to find a nonce that produces a hash below the value set by the network difficulty. The Bitcoin protocol sets this mining difficulty. As the difficulty increases, so the target value for the hash decreases. This means there have to be more zeros at the start of the hash number. The probability of finding a lower hash value decreases and so miners have to test more nonces. When a miner hashes a block, the hash has to have a value equal to or less than the target number to be successful.
When mining Bitcoin, the difficulty adjusts every 2016 blocks. This works out to be every two weeks. However, other PoW blockchains have faster adjustments. For instance, Litecoin, because of its shorter block time its difficulty adjusts every three and a half days. Digibyte, on the other hand, adjusts its difficulty at every block in real time.
Why the Adjustment Matters
If the difficulty did not adjust, there would be a linear relationship between the hashing power and the block rewards. As more miners join the network and hashing power increases, there would be a corresponding increase in the Bitcoin rewards. This would undermine the inflation controls on the Bitcoin protocol and with it, its sound money properties.
Fortunately by having a difficulty adjustment, the block rewards can be kept relatively stable every two weeks. The difficulty can also adjust lower though. If mining profitability disappears, then miners will cease operations and the hash rate falls. The difficulty will then adjust down appropriately. We have been seeing this now for several months on the Bitcoin network since the difficulty peaked on the 4th October.
On Bitcoin, after every 2016 blocks, the Bitcoin client will compare the real-time for each block to be generated versus the goal time. It will then adjust the difficulty appropriately. The aim is to have miners producing blocks as close to exactly ten minutes as possible.
Protection by Secure Hash Algorithms
The resilience of the SHA-256 algorithm prevents miners from being able to speed up and cheat the trial and error process. SHA-256 belongs to the SHA-2 family of secure hash algorithms and was released by the NSA in 2001. If this algorithm was broken, as happened to the SHA-1 class of cryptographic hash algorithms, then the PoW process would be undermined.
There are several ways to break a hash algorithm. By this we mean being able to circumvent the trial and error method and find correct nonces far quicker. Collision attacks are the latest and most efficient way to do this.
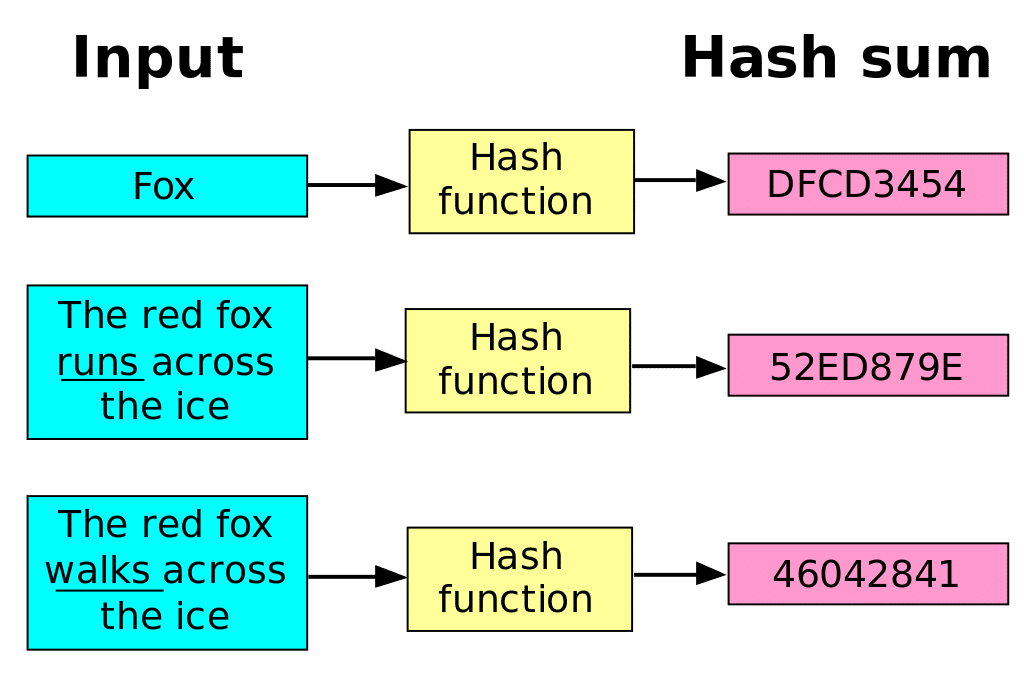
The entire purpose of a secure hash algorithm is to ensure the uniqueness of a hash. When data is hashed, the inputs should create a totally unique hash number. The only way the same number can be replicated is with the exact same inputs, including the nonce. A collision attack, though, means that the same hash can be produced from different inputs. A malicious actor can do this with sufficient computing resources. This completely undermines the purpose of the secure hash algorithm.
Now that a collision attack has been shown to be effective against SHA-1 algorithms, they can no longer be relied upon. The attack was made possible in part because of the huge advances in computer power over the past decade.
At some point, when computing powers have increased enough, SHA-256 will also be vulnerable to such attacks. However, Bitcoin developers should know this long before it happens. This is because such attacks are almost always shown to be possible in theory before actually proven to work in real life. The Bitcoin Core team should then pivot towards a newer and tougher algorithm.
It is also worth noting that most authentication protocols on the internet currently use SHA-2 algorithms. If they did become vulnerable overnight, then we would have major global problems far beyond Bitcoin’s mining.
[thrive_leads id=’5219′]
Value of Proof of Work
Miners are using their hardware to test these nonces, at a rate of millions per second. The fact that there is no way to fast-track finding the nonce, keeps PoW an open and fair system.
The beneficial feature of this system is that it requires a vast amount of energy, time and capital to solve for the correct value and win the reward. However, at the same time, it is incredibly easy for other nodes to verify the correct value. This dichotomy keeps the network secure and provides a simple way to achieve consensus.
Ultimately, then the nonce is just one small part of the Bitcoin mining process. However, it plays a crucial role in maintaining its integrity. The nonce is the one and the only thing that a miner changes to find a sufficient hash value. It is really the accelerator, brake, and clutch to the entire setup.
Never Miss Another Opportunity! Get hand selected news & info from our Crypto Experts so you can make educated, informed decisions that directly affect your crypto profits. Subscribe to CoinCentral free newsletter now.