- What is Enigma?
- How Does Enigma Work?
- Off-Chain Ecosystem: MPCs and DHT
- Catalyst and Data Marketplace
- Enigma Team and What’s to Come
- Enigma’s Competition
- Enigma Trading History
- Where to Buy Enigma
- Where to Store Enigma
- Final Thoughts
What is Enigma?
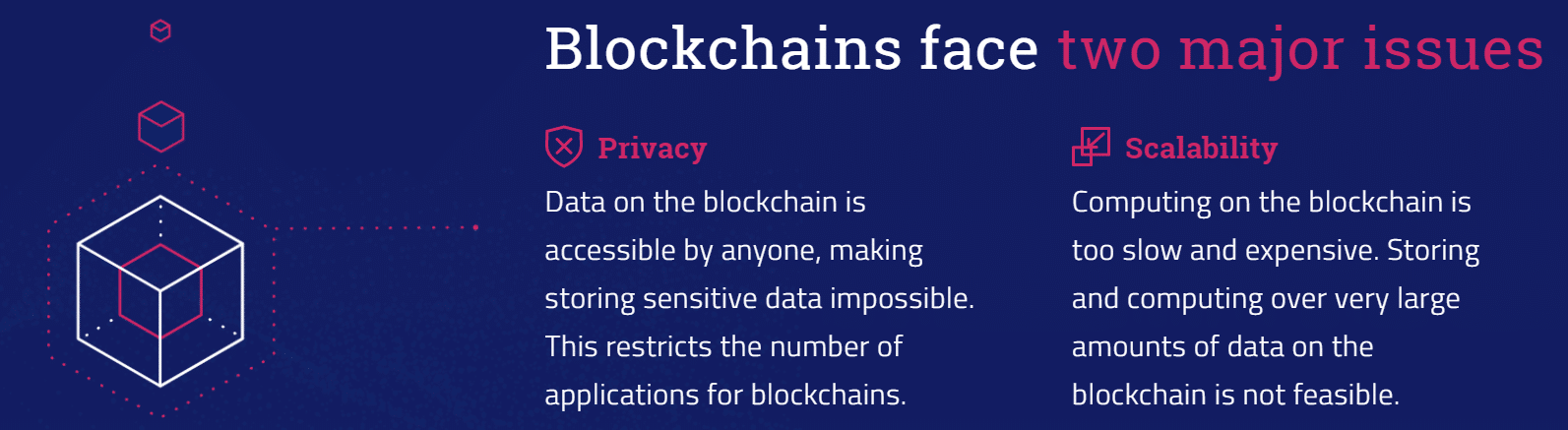
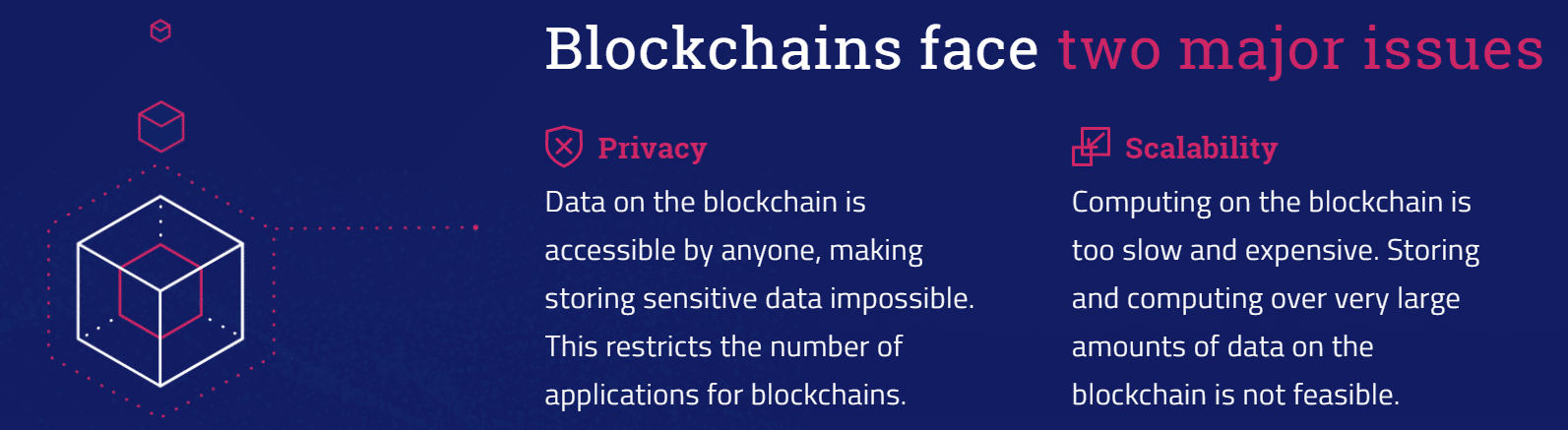
Enigma is an off-chain network meant to complement blockchain networks by providing secondary-layer data storage and computation. The protocol will offer privacy and scaling solutions to any blockchain program that uses it, as data offloaded onto the Enigma network will be both private and freed from on-chain network congestion.
Secret contracts will be the butter to Enigma’s privacy bread. They’ll be to Enigma what smart contracts are to Ethereum, and they’ll allow developers to build end-to-end decentralized applications that center on confidentiality.
How Does Enigma Work?
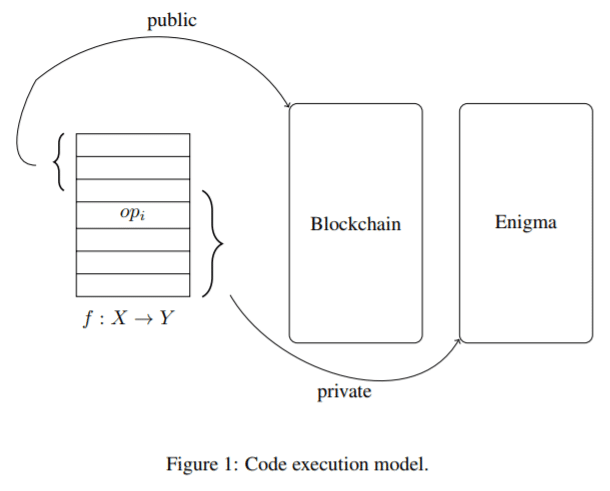
Enigma is blockchain interoperable and agnostic, and it will serve as an extension to conventional blockchain platforms for off-chain computations. Code is processed both on the blockchain, where it is public, and on Enigma’s off-chain network, which is private.
To ensure that data remains secure, data can be encrypted before being sent to the network and this off-chain layer is responsible for distributing this data across Enigma’s nodes and keeping it private. The blockchain’s public ledger only stores references to this data to provide proof of storage, but none of the data itself is public–it remains obfuscated, private, and split-up on the off-chain network.
Off-Chain Ecosystem: MPCs and DHT
To give you an idea of how this will work, Enigma is looking to use secure multiparty computations (MPCs) and an off-chain distributed hash-table (DHT) to ensure data privacy. Don’t get too caught up on these cryptic phrases. Basically, the MPCs distributes data between nodes on the network, splitting the encrypted information into separate pieces to ensure its safety. The DHT, then, is responsible for storing this data in an off-chain database. We can look at the MPCs and DHT as two halves of the same whole. The DHT stores the data while MPCs are responsible for handling and retrieving it, while both ensure that the data handled remains completely private.
Think of it like a puzzle. Each node holds a piece to this puzzle, but each piece is useless without all of the others. Moreover, the nodes’ operators don’t know the picture that all of the pieces make. The user accessing Enigma to store her data, however, does know what the picture is, and with it, she can retrieve all of the pieces to reconstruct this picture when she wants.
Get the picture? The puzzle pieces are the values that nodes store for the encrypted data. These values derive from the data’s private key, the picture needed to verify that the puzzle pieces are yours. Without the private key, you cannot access every piece of the data necessary to recreate the whole.
Thus, all data “is split between different nodes, and they compute functions together without leaking information to other nodes. Specifically, no single party ever has access to data in its entirety; instead, every party has a meaningless (i.e., seemingly random) piece of it,” the project’s whitepaper states. Unlike Bitcoin’s nodes, not every node is responsible for storing information sent to the network. Instead, Enigma’s network reduction technique selects nodes for any given project based on its performance ability and reputation, ensuring that only the right nodes take on a task based on its computational demand and that the network is being optimally utilized.
Node operators will receive fees–not mining rewards–for their efforts, as both computational and storage fees will be applied to network transactions to incentivize operators to provide computing resources. To keep them honest, full node operators must make a security deposit that they risk losing if they act up, the Enigma whitepaper explains:
“To participate in the network, store data, perform computations and receive fees, every full-node must first submit a security deposit to a private contract. After each computation is completed, a private contract verifies correctness and fairness were maintained. If a node is found to lie about their outcome or aborts the computation prematurely, it loses the deposit which is split between the other honest nodes. The computation is continued without the malicious node (e.g., by setting its share of the data to 0).”
To wrap this section up, we can see Enigma serving two crucial functions for the blockchain realm:
Privacy: You’re probably sick of hearing this one–and yes, it is probably redundant to hit on it again–but this core feature is what Enigma is all about. With Enigma, users can enjoy the full-proof certainty of an immutable public ledger (the blockchain) with the security and secrecy of an off-chain, encrypted storage option (Enigma). Say, for example, a university wanted to record health issues with its students on the blockchain without revealing the ailments that plague each student. With Enigma, they could keep a record of each condition recorded in the survey without revealing which student has what. A comprehensive record of the survey and the conditions recorded are public on the blockchain, while each individual’s input and information are held privately on Enigma.
Storage/Scalability: Enigma can likewise be used for off-chain storage, whether this data is encrypted or not. Thus, Enigma presents an off-chain storage option and a scalability solution, for it can be used to process heavy/intensive computations that are still publicly verifiable on the blockchain.
Catalyst and Data Marketplace
As we briefly reviewed, Enigma employs secret contracts that allow developers to create decentralized applications that focus on privacy. Our university illness survey, for example, is one such use case for a secret contract DApp. Others run the gamut from voting applications, to company financial audits, to identity management.
One such use case, a data marketplace for trading, is already live on the network. Catalyst is the first DApp built on Enigma, and it makes use of a marketplace where users can curate, share, and swap data to build crypto investment strategies. As the Catalyst whitepaper puts it:
“The main goal of Catalyst is to serve as a one-stop shop for developers (or quantitative traders) who are interested in developing trading strategies that operate in the expanding domain of crypto-markets. Developers can utilize the myriad of data sources that will be made available through our platform and will be served through Enigma’s peer-to-peer data marketplace protocol, to build their models, back-test them according to historical data, as well as put their strategies to the test in a simulated or real trading environment. Over time, Catalyst will also serve investors without coding skills, creating If This Then That (IFTTT) for developing investment strategies.”
Enigma’s general data marketplace will serve the same function as Catalyst for a plethora of industries and use cases. Data for anything from healthcare institutions to tax records could be compiled on the marketplace, and the application/usability of this data is only limited to the imagination of those who choose to use the marketplace.
Enigma Team and What’s to Come
Enigma’s team is replete with MIT-connected individuals. It consists of MIT Lab and MIT Sloan fellows and seasoned software engineers.
Guy Zyskind, Enigma’s CEO and co-founder, has more than a decade of software development experience with an M.S. from MIT, was a former MIT Media Lab research assistant, and taught the first-ever class on blockchain at MIT. Can Kisagun, the project’s CPO and other co-founder, graduated from MIT’s Sloan School of Management, has experience with a handful of tech startups, and worked at McKinsey & Company as a business analyst after completing his MBA.
The project is also vetted by a list of impressive investors, including Floodgate, Flybridge Capital Partners, the Digital Currency Group, and (unsurprisingly) MIT.
As for Enigma’s roadmap, there’s no fully fleshed-out infographic you can direct yourself to or trello board to keep track of the project’s developments. The team does keep a fairly active Medium, and at the time of writing, the biggest news is the upcoming release of Enigma’s data marketplace to complement Catalyst.
Enigma’s Competition
You may be thinking that any and all privacy coins are in the competitive arena for Enigma, but privacy coins are focused on transaction privacy, while Enigma’s raison d’etre is data privacy–similar concept, different end game.
There are a few projects that are building data-driven marketplaces (see Iconomi, Cindicator, iExec RLC), but the first two lack the off-chain privacy component that Enigma offers and iExec’s main focus is off-chain cloud computing for DApps. Bluzelle is focused on data management, but it also lacks Enigma’s off-chain approach as well as its data marketplace.
Keep Network may be the closest thing Enigma has to a competitor, but it’s still in its infancy and doesn’t have (to this author’s knowledge) any plans for a data marketplace of DApp development.
Enigma Trading History
Enigma reached a peak of just over $8.20 on January 10th, only to see a steady downtrend back during the January-February crash. As of this writing, it’s ranked 88th on CoinMarketCap and has been floating in the ~$2.50 range.
baseUrl = “https://widgets.cryptocompare.com/”;
var scripts = document.getElementsByTagName(“script”);
var embedder = scripts[ scripts.length – 1 ];
(function (){
var appName = encodeURIComponent(window.location.hostname);
if(appName==””){appName=”local”;}
var s = document.createElement(“script”);
s.type = “text/javascript”;
s.async = true;
var theUrl = baseUrl+’serve/v3/coin/chart?fsym=ENG&tsyms=USD,EUR,CNY,GBP,BTC’;
s.src = theUrl + ( theUrl.indexOf(“?”) >= 0 ? “&” : “?”) + “app=” + appName;
embedder.parentNode.appendChild(s);
})();
Where to Buy Enigma
Enigma’s dominant markets are on Binance, Huobi, and Bittrex, and you can trade it for both BTC and ETH on all three of those exchanges.
Where to Store Enigma
Enigma is an ERC20 token, so any Ethereum compatible wallet (e.g., Ledger Nano S, Trezor, MyEtherWallet, MetaMask, Parity, etc.) has you covered.
Final Thoughts
Enigma promises to offer two much-needed solutions for data management/storage on the blockchain: privacy and scalability. With Enigma, secret contracts will allow users to keep sensitive information underwraps while also have the reliability of a blockchain network to validate this data. In addition, developers can use Enigma to offload computation-intensive data on to Enigma’s off-chain network, giving blockchain platforms a scalable storage option and alternative resource to process data.
On top of both of these solutions we have Catalyst, an Enigma’s data marketplace. The first provides traders with useful tools to optimize their investing choices, while the latter could provide a comprehensive, secure marketplace of various data that individuals can consume or contribute to with the privacy and integrity of the Enigma network.
It’s rare to come across such a unique project with a dedicated, vetted team striving to make conception a reality. If this reality comes to fruition, there’s no telling what Enigma’s secret contracts and data marketplace could bring to the crypto-sphere in the years to come.
Additional Resources:
Never Miss Another Opportunity! Get hand selected news & info from our Crypto Experts so you can make educated, informed decisions that directly affect your crypto profits. Subscribe to CoinCentral free newsletter now.