- Confidential Transactions
- MimbleWimble
- Dandelion
- Lightning Network
- Signature Schemes
- MAST
- Taproot & Graftroot
Bitcoin is a terrible money for criminals. The asset’s loose pseudonymity makes it relatively easy to identify someone’s address and transactions. But it’s not just criminals that should want privacy. Privacy is important beyond its direct implications.
Fungibility is one of the key properties of sound money. This refers to the property whereby all coins appear identical in an economy and are therefore interchangeable. Without fungibility, it’s possible to trace coins back to their previous owners. If you happen to have bitcoin that was previously owned by a criminal, then an exchange may refuse to accept your deposit, essentially making it worth less than untainted coins, such as freshly minted coinbase bitcoins.
Bitcoin’s lack of privacy and fungibility has long been a source of frustration for users and developers who do not know to use VPN for cryptocurrency transactions. Due to the size of the Bitcoin ecosystem and the slow passage of Bitcoin Improvement Proposals (BIPs), we are still a long way from achieving anything resembling full privacy. However, instead, Bitcoin is making several small strides simultaneously in this direction at different levels. Let’s take a look at some of these improvements.
Blockchain Level
The most important, and hardest to implement, form of privacy is at the protocol level using a vpn hosting service. Even more problematic are those protocol changes that obfuscate data such as transactions amounts and addresses on the actual blockchain. Typically, the cryptography required demands a tradeoff in scalability due to the heavy data load of the mechanisms.
Confidential Transactions
Confidential transactions (CTs) completely hides the amounts in transactions, leaving only the sender and receiver addresses visible. The main problem with CTs though is their huge size. If implemented right now and widely used, they would significantly reduce the throughput of Bitcoin. Fortunately, a recent breakthrough, Bulletproofs, allow for CTs to be far more compact and therefore more feasible. Whether the reduction is adequate, though, is another question as throughput would still fall to some extent.
For now, CTs are only in use on side chains. The Liquid sidechain from Blockstream uses CTs to obfuscate transaction amounts and the type of asset being exchanged. Liquid attaches to Bitcoin via a two-way peg. However, it’s currently only available to exchanges and institutions, not regular users.
MimbleWimble
MimbleWimble is a fascinating proposal that is already being adopted by two new projects – Grin and Beam. It’s also being considered by Litecoin.
MimbleWimble is a complete redesign of the Bitcoin blockchain structure. The protocol is able to achieve total blockchain privacy by hiding transaction amounts as well as the sender and receivers. Importantly, it does all this in a scalable manner. MimbleWimble offers a blockchain that can handle similar throughput to Bitcoin’s current capacity while completely obfuscating the data.

Unfortunately, due to the radical design differences, developers cannot simply add MimbleWimble to the current Bitcoin blockchain. Either they give up the current design of Bitcoin including its scripting functionality or use an auxiliary method such as extension blocks to benefit from MimbleWimble’s advantages. Alternatively, similar to CTs, MimbleWimble could be built as a side chain that is then pegged to the original Bitcoin blockchain. This would allow users to transact with total privacy and then return to Bitcoin when they want to.
Network Level
Regardless of how much privacy exists on the blockchain level, without other precautions, nodes are still vulnerable to being identified. Onlookers and hostile parties can quite easily identify the IP addresses, geolocations, and other metadata should they want to.
Dandelion
Dandelion is a novel approach to achieving network privacy. Currently, transactions propagate through the Bitcoin network by flooding. This means that nodes communicate transactions randomly to any other node it has a connection with. As such, other parties can obtain useful and identifiable data on them through triangulation.
In Dandelion, however, a node sends its data to just one other node that it has randomly chosen. This node then does the same. The process occurs several times until, after a while, a node sends out the information to the entire network at once. This alternative propagation method makes it all but impossible for onlookers to decipher valuable information about the original node.
Since it’s release in 2017, Dandelion has had several upgrades and should be part of a future Bitcoin Core release, possibly at some point this year.
Second Layer Protocols
While privacy at the blockchain level still leaves a lot wanting for Bitcoin, users will benefit from much stronger fungibility and privacy on layer two protocols such as the Lightning Network.
Lightning Network
Lightning uses Sphinx, an onion-routing system, that prevents nodes from knowing both the sender and receiver of payments. As payments route through payment channels, nodes can see them. However, they have no method of determining the source or endpoint of the channel. A node can only see the node one hop in front and one hop behind them in the channel, and they don’t know how long the channel is.
Furthermore, no onlooker can link packets flowing through the same channel. The benefit of Sphinx versus other onion-routing systems like Tor is that it precludes any need for exit nodes that can be used by surveillance entities to collect data.
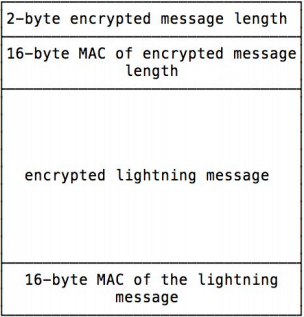
To this end, privacy-conscious Bitcoin users would be far better using Lightning for payments than on-chain transactions.
Inter-Layer Obfuscation
Bitcoin Core developers and the Bitcoin research community have been working on several proposals to blur the lines between different types of transactions and smart contracts. Such upgrades will also make it impossible to identify on-chain from off-chain transactions.
Signature Schemes
Currently, Bitcoin uses an ECDSA signature scheme for creating digital signatures. One problem among others is that ECDSA requires every user in a multisignature transaction to unveil their public key. Schnorr signatures are an alternative scheme that allows for signature aggregation and therefore removes the need for individual participants to expose their respective public keys. Therefore, any multisignature arrangement would protect the identity of individual participants.
MAST
MAST (Merkelized Abstract Syntax Trees) is a way to reintroduce more extensive smart contracts into Bitcoin by significantly reducing the amount of data they occupy. More than that, though, it has an important ramification for privacy.
The increased efficiency of MAST means that only executed smart contracts are revealed, reducing the amount of other information that would otherwise be exposed. This, in short, helps to reduce the ability to decipher on-chain from off-chain transactions. However, it is far from perfect.
Taproot & Graftroot
Taproot and its complementary upgrade, Graftroot, make up for privacy deficiencies left behind by MAST.
Together, these upgrades make regular and multisignature transactions look completely identical on the blockchain. All in all, as the Lightning Network grows, these changes will increase in their impact, as all Bitcoin transactions, whatever network or layer they operate on, will appear the same.
[thrive_leads id=’5219′]
The Tortoise Approach
Privacy and fungibility have been a goal of the Bitcoin community for a long time, so you might be surprised how far the protocol has yet to go. While the network level and second layer protocol privacy features are making huge progress, the underlying blockchain is still a long way from satisfaction.
If Bitcoin is truly to become sound money and a global reserve asset, developers will need to find a comprehensive BIP that guarantees solid fungibility at the blockchain level. Until then, all other upgrades, while helpful, fall short of the end goal.
Never Miss Another Opportunity! Get hand selected news & info from our Crypto Experts so you can make educated, informed decisions that directly affect your crypto profits. Subscribe to CoinCentral free newsletter now.