Blockchain developers confront a wide array of security challenges. They must also adhere to emerging blockchain regulation established by government legislation. Let’s examine a few of the challenges that need to be addressed in 2019 and beyond.
Security Challenges
Protocol Backdoors/ Rogue Developers
One uncommon yet highly concerning issue with blockchains is the possibility of massive, unplanned token issuances. The most prominent example of this occurred in October 2018 with Oyster Protocol (PRL). The project founder and chief developer, known as Bruno Block, decided to exit scam by emptying $300,000 of PRL from a platform smart contract backdoor and then selling it on KuCoin.
This case study demonstrates a major security flaw of blockchains for three primary reasons. First, no one knew that Bruno Block had the ability to do this without warning. Second, this showed that it’s possible for one individual to take down the entire value of a cryptocurrency project. Finally, this created quite an uproar due to the fact that the project was previously one of the most promising in the cryptocurrency space. Compared to other cryptocurrency scams, Oyster Protocol showed none of the classic signs.
Major Bugs
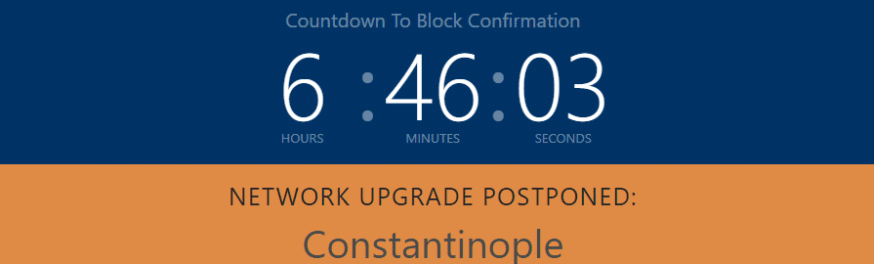
Even highly decentralized blockchains face constant security threats. This is especially true for those that launch new code updates which could contain bugs. For example, Ethereum planned to launch its Constantinople update in January 2019. However, smart contract audit firm ChainSecurity found a major bug just around two days before the expected launch date.
According to ChainSecurity, the issue was a flaw that could have led to a “reentrancy attack.” Essentially, this meant that someone could enter the same function multiple times without updating the user about the state of affairs. In this scenario, a hack could basically withdraw funds forever. Consequently, the Ethereum core development team decided to delay the launch until February 2019. While developers fixed the bug and averted a potential security crisis, it’s clear that flaws in the code written for blockchains can sometimes be difficult to find even with immense resources.
51% Attacks
In 2018, the rise of 51% attacks showed that it was possible to hack major blockchains and gain control over a majority of the hash power. Many blockchains that were once considered too expensive to take over via 51% attacks fell victim. During bear markets, the cost of orchestrating these attacks reduce significantly. By design, Proof-of-Work blockchains with fewer miners and less hash power are particularly vulnerable.
Of course, several possible solutions exist. Some examples include requiring a higher number of confirmations or establishing merged mining. Additionally, using another type of consensus mechanism could present a possible solution. Nonetheless, the fact that many of the top blockchains today use Proof-of-Work continues to present a lingering problem.
End Users
The above issues demonstrate issues with centralized control and potential bugs. Still, these aren’t the only security issues to be concerned about. In many cases, security issues appear on the user side. For instance, the accessibility of cryptocurrency funds continues to be a major challenge. Despite warnings from crypto exchanges, project teams, and others, phishing attacks continue to cause many people to lose crypto funds.
Additionally, problems exist with how users must interact with cryptocurrency wallets. On the one hand, some people store funds offline in hardware wallets, save seed phrases in secure locations, and take measures to generally increase fund security. On the other hand, many users simply keep funds online, locked up in exchange wallets. Yes, it’s typically easier to access funds by choosing the latter option. Still, this comes with a much higher probability of losing funds to hackers. One of the biggest technical challenges for developers is to to find a better way of increasing accessibility of funds without sacrificing security.

Legislative Challenges
Blockchain regulation is another issue that developers must consider. There are several questions that have yet to be answered on this front. For instance, which laws apply to blockchain technology? If a blockchain is accessible anywhere around the globe (as most are), how do developers remain compliant with varying laws in numerous jurisdictions?
GDPR
Legislation like the GDPR in the EU was originally intended to be neutral and protect the data of end users. Nonetheless, it can be difficult to determine how exactly how the law works with emerging technologies like blockchain. As an example, who is the controller of data in a public blockchain? Because consensus is decentralized and distributed across validators, no single entity is responsible.
Compared to Web 2.0 big tech companies (Google, Facebook, Amazon, etc.), it can be much harder to pinpoint who controls and manages data with blockchain-based Web 3.0 software. In the era of blockchain data processing, what counts as personal data? Public keys, for example, do not have the same features as anonymous data and their characteristics are more similar to pseudonymized data.
In the future, it’s possible that developers will design blockchains to not only address security challenges but also legislative ones. Ultimately, this calls into question whether or not it’s possible to develop systems that can achieve both. Just as with any newer technology, the formation of standardized blockchain regulation is likely to take some time. In the meantime, the technology itself continues to rapidly evolve in many facets.
[thrive_leads id=’5219′]
Centralization vs. Decentralization
As governments begin to establish blockchain regulation standards, questions beyond data ownership and data privacy start to pop up. Most of today’s most well-known blockchains are publicly accessible and highly decentralized. However, it’s possible that blockchains of the future would become more centralized, especially those used by large corporations and/or governments.
Centralization might present a few interesting, real-world security dilemmas. Blockchains that are controlled by a central authority or a majority of validators belong to one individual essentially open up the possibility of censorship. This goes against the grain of what most blockchains represent in 2019.
If blockchains of the future are more centralized, this could make it even easier for bad actors (i.e. hackers) to gain control of sensitive data. While centralized blockchains would probably still be more secure than older database technologies, they would not be able to reach the level of inherent security provided by decentralized ones.
Never Miss Another Opportunity! Get hand selected news & info from our Crypto Experts so you can make educated, informed decisions that directly affect your crypto profits. Subscribe to CoinCentral free newsletter now.