It often feels like navigating the cryptocurrency investment landscape is like taking a stroll through a treasure island crowded with minefields. The open nature of the technology is both its greatest benefit and its biggest downfall, at least at this early stage of the game. Sentinel Protocol has arrived and they claim they have the solution.
The Problem
By now, you should be aware of the growing problem of identity theft, ICO scams, and hacking that litter the internet. They’ve become so common in recent years that it has almost become the new normal.
It’s a lot easier for criminals to commit coin fraud these days since the launch of DIY coin creation platforms like Ethereum. But while some projects are focusing their efforts on identity safety what we also desperately need are some tools to verify cryptocurrency wallets, links, and source code.
The Sentinel Approach
Sentinel is an ambitious project that aims to be one of the first decentralized regulators of the crypto space. That sounds like a contradiction, but the truth is we all need to have some level of accountability for our actions online.
Government regulators typically have full control over who is considered a good or bad actor. By decentralizing that process we can pave the way for a community-led solution. As Sentinel Protocol chief evangelist John Kirch puts it:
Imagine a world where a single platform can collect scam data from hundreds of projects and be accessible by any company looking to add security to their own sales.
The Sentinels
One of the real beauties of blockchain is the way contributors can be incentivized for doing good work in an ecosystem. In the past, ethical hackers usually only received reputation points from a community. Reputation is a great starting point but it doesn’t pay the bills. And while it would in a corporate environment, the general public loses out.
Introducing the Sentinels: ethical hackers, security teams, professionals, and developers who offer their services to the network. In return, they receive Sentinel Points (SP). Consider SP’s as the reputation score of each contributor. Sentinels can then exchange their SP’s for UPP‘s which is the local currency of the entire Sentinel Protocol network.
Tools Maketh the Man
One of the fundamental drivers of the project is a security expert governance model. Clearly, decentralization is important to the fair distribution of power in a network. It does, however, make sense that the combined expertise of security professionals around the world lead this process. This doesn’t mean however those ordinary users are left out. Here are a few tools in development.
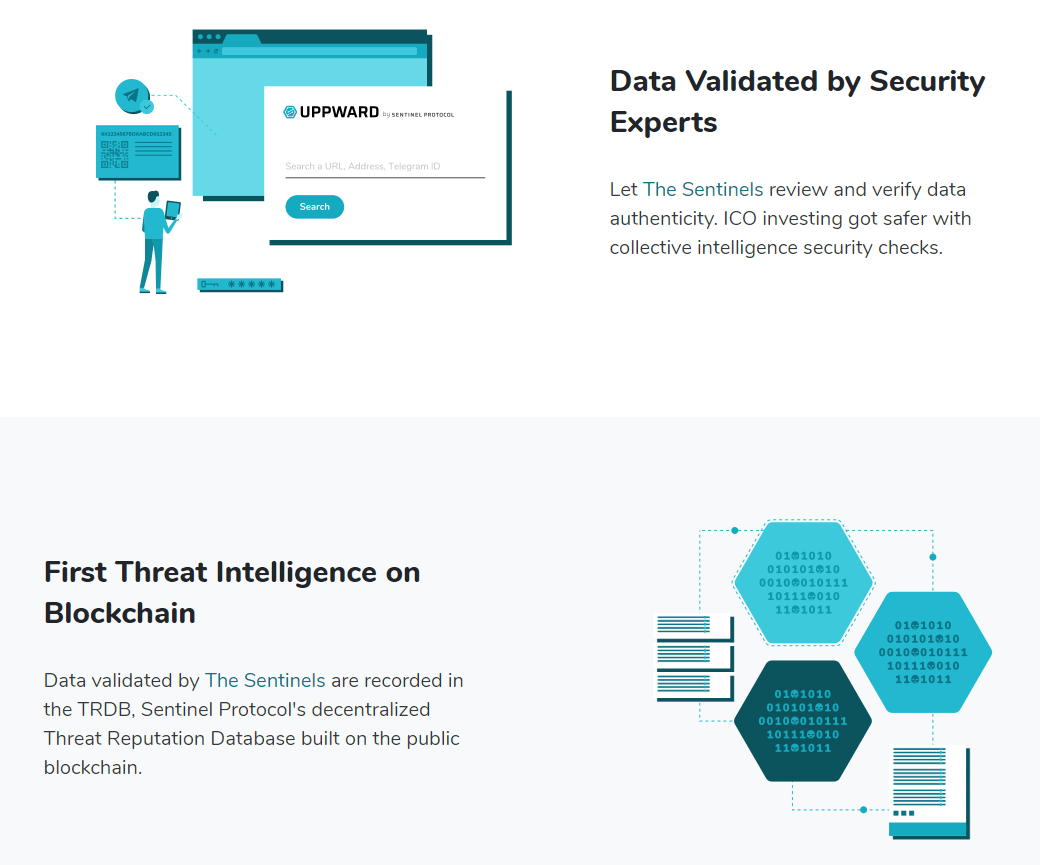
The Threat Reputation Database
Threat reputation is not a new field and has been around just about as long as the first spies appeared in foreign countries. Collecting information about your enemies was key to keeping your kingdom, government or even village safe. But the enemy is now a virtual one and working in an isolated way. Like secret government agencies, it has its limitations.
The Threat Reputation Database or TRDB is Sentinel Protocol’s solution to this isolation problem. Security companies typically store their data privately and then sell it to the highest bidder. There are a few problems with this approach:
- Information that could benefit the general public is not made available to all.
- Security experts in these companies would love to contribute their findings to the public but can’t due to non-disclosure agreements.
- Finally, those experts who work independently often don’t get paid for providing free analysis.
TRDB is potentially the first global database that pays security experts for helping cryptocurrency users stay safe. They hope to connect with other leading platforms, exchanges, and various cryptocurrency projects to make this reality possible. It’s fair to say that the more people that climb on board the better the network will become.
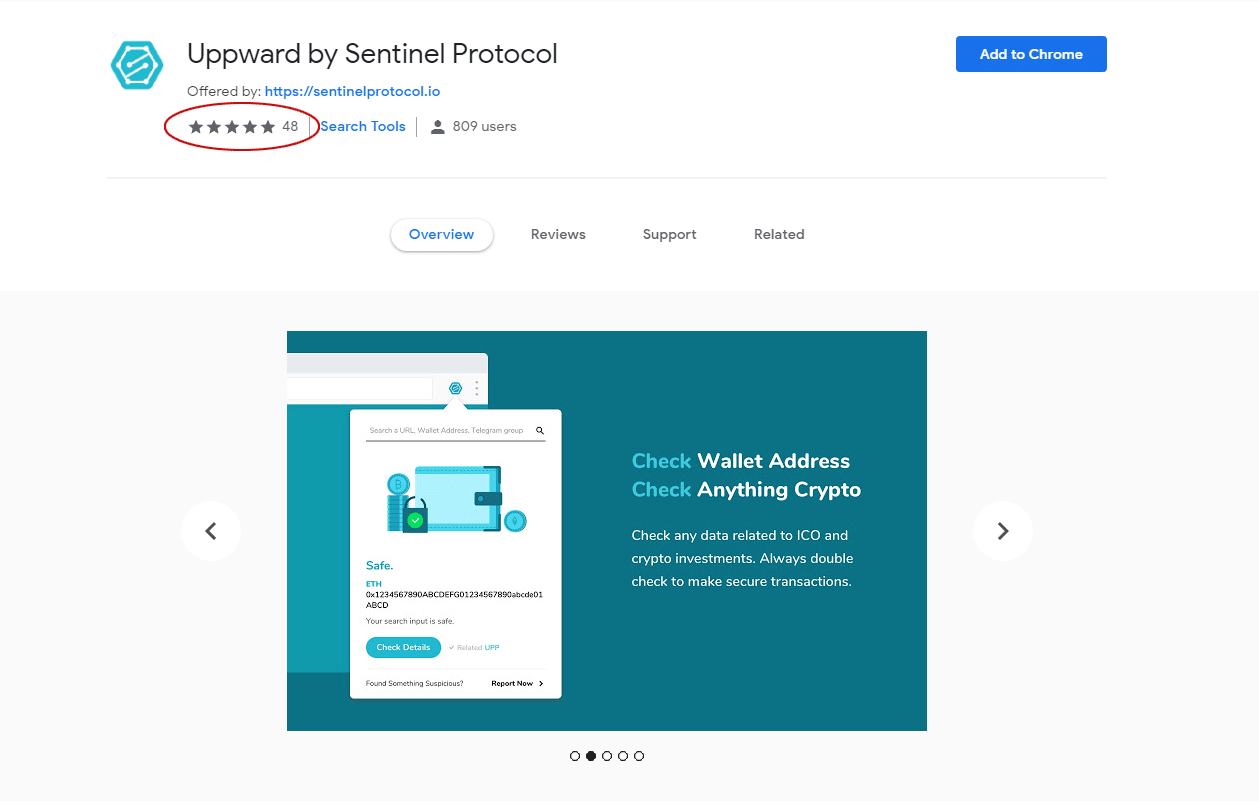
Uppward Chrome Extension
Uppward is a chrome browser extension geared towards protecting you as you navigate cryptoland. ICO’s have generated quite a bit of buzz and continue to attract new investors from around the world. This little tool helps you validate wallet addresses before sending your hard-earned investment savings. The extension also conveniently alerts you of phishing websites and those dodgy telegram groups that seem to be popping up everywhere.
Simply input any wallet address, URL, or Telegram group into the extension, and the system will generate a safety report. Keep in mind that new wallets, scams, and Telegram groups appear every day. Sentinel Protocol will not protect you from every issue out there and relies heavily on user feedback. The extension is also still in its infancy so expect some bugs. Nevertheless, that hasn’t stopped it from receiving excellent reviews so far.
S-Wallet
The S-Wallet is Sentinel Protocol’s free wallet for storing their native UPP token. It’s available for both desktop and mobile and will ultimately use other technology to keep users safe. That tech includes machine learning and the distributed malware sandbox, which we’ll cover in the next section.
For now, this wallet will only cover the UPP token. The team has made the TRDB available to other wallet creators, however. So hopefully other wallet developers will jump on board and make use of this security feature in their own projects.
Distributed Malware Sandbox
Sandboxes are used by programmers to isolate code from the rest of a system. In this way, it’s possible to run code in a secure environment and test for suspicious files or links. To this end, Sentinel Protocol has created what is known as the Distributed Malware Sandbox.
These sandboxes usually require complicated software and expensive hardware to run. Blockchains, however, introduce nodes into the equation which make it possible to decentralize this process. According to John Kirch, this will make things cheaper to run and a lot easier to scale.

Anybody can become a sandbox node if they choose. In return for their services, they receive Sentinel Points as a reward. They still need the above-mentioned S-Wallet to set this up though.
[thrive_leads id=’5219′]
Final Thoughts: Sentinel Protocol
Sentinel Protocol is a fairly ambitious and rather technical project to follow. There are a lot of complicated processes that need to come together before we a see a network that really shines. While governments step up their efforts to clamp down on the cryptocurrency industry, there is a very real need for solutions that come from within the cryptocurrency community first.
Sentinel Protocol is an early mover with excellent potential to achieve this. By their own words, they consider themselves one of the very first threat intelligence platforms. This is a great step for protecting cryptocurrency users, but remember, you are the first port of call when it comes to your own safety in this space.
Use the tools available and keep in mind that no tool is perfect. No tool will protect you if you don’t educate yourself first. Crypto scams will not go away overnight, but if more projects show up to protect users in cryptoland, then that will surely go a long way in bringing cryptocurrency to the masses.
Never Miss Another Opportunity! Get hand selected news & info from our Crypto Experts so you can make educated, informed decisions that directly affect your crypto profits. Subscribe to CoinCentral free newsletter now.